The COVID-19 pandemic has taken a huge toll worldwide for both individuals and economies. As a precaution, many countries have implemented strict lockdown measures such as closing schools, restaurants and borders, while mask-wearing in public and social distancing have become a must.
The enforcement of these policies, along with the extensive testing of populations has helped to minimize infection rates. However, when an individual is found to be infected with the coronavirus, the race is on to find those who have come into contact with them, as these people could be carriers or even be infected.
This has led to hundreds of coronavirus contact-tracing mobile applications being developed worldwide and backed by various governments and national health authorities, as well as guidelines by the EU and special protocols developed by the two major smartphone OS vendors Apple & Google.
In some places, the usage of such applications have been made mandatory for people who want to gain access to public spaces. And while the technology and algorithms differ between applications, the promise of most coronavirus contact tracing apps is the same:
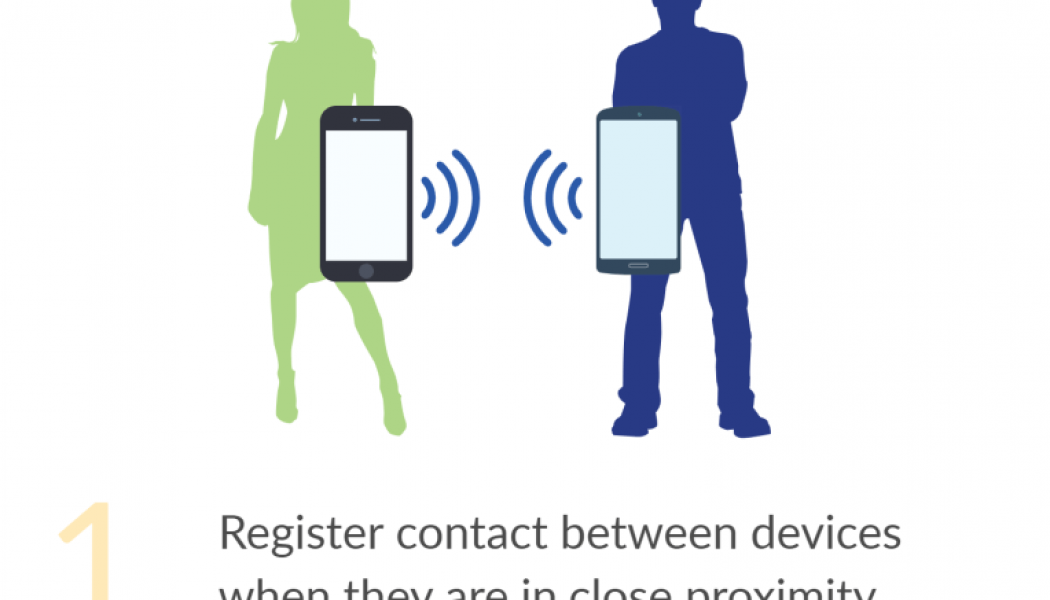
- The ability to detect close contact between individuals (i.e. within several meters) over a period of time.
- When a person tests positive for coronavirus, they can use the application to advertise either their locations or the Bluetooth identifiers from registered contacts.
Applications notify users that have appeared to be in close proximity with an infected person. The information around contacts made by the users of the applications is eventually shared with the local health authority, and/or with other users.
Of course, if such a system is to be effective in breaking infection chains, the application must have high adoption rates.
These observations, naturally, raise many questions around the privacy of individuals’ data that the app may access, and the potential abuse of such systems. Here’s our overview of the existing approaches for contact tracing technologies, and how they deal with these privacy and security concerns.
Privacy and Security Concerns
Some are concerned that contact-tracing apps are surveillance tools that invade individual privacy and disclose sensitive information. Therefore, any such app and tracing system must maintain a delicate balance between privacy and security, since poor implementation of security standards may put users’ data at risk.
This comes down to questions on what data is collected, how it is stored and how it is distributed. For example, is the data encrypted? Is there a proper authorization/verification process to protect against abuse? Is user anonymity preserved given that personal identifiers such as phone number, name and IDs are being collected?
Another aspect is user consent – does the user submit their data voluntarily, or is the data being collected and uploaded without the user’s knowledge? The two most widely used techniques for detecting proximity between two devices are GPS and the Bluetooth Low Energy (BLE) protocol.
GPS location tracking
With this method, the apps obtain a user’s GPS position periodically and save a log of the user’s locations and timestamps. This data may be later intersected with other users’ location logs.
This approach offers the flexibility to analyze the geography of the infection spread and gives more options to governments and health authorities to localize infected regions and apply prevention policies accordingly. However, this also gives away very sensitive information, revealing users’ travels and locations over the previous few days or weeks.
Examples of mobile applications that utilize GPS logging are MIT’s SafePaths, Cyprus’ CovTracer (which is based on SafePaths), Israel’s Hamagen and India’s Aarogya Setu.
Bluetooth Low Energy (BLE)
Here, each device broadcasts pings over BLE. These pings are registered by other devices that are in Bluetooth range based on duration and signal strength. To work, both devices must be running the contact tracing app.
This technology is widely used in coronavirus tracing applications, as it offers more privacy – the only info usually transmitted over Bluetooth is a cryptographic identifier that changes frequently and does not expose user identity. In addition, BLE randomizes MAC addresses sent in a packet over the air and changes it every few minutes, making it difficult to track devices.
When a person tests positive for COVID-19 they can publish all the IDs collected in proximity to them. Each user can then check whether one of the IDs belongs to them and find out when, and for how long, they were in proximity with the infected person. Since the IDs are anonymized, only the end-user can affiliate them to their device.
The downside of this approach is its inability to map the infection geographically. Despite this, BLE is by far the most popular method, and among the applications using BLE for contact tracing include UK’s “NHS COVID-19”, Singapore’s TraceTogether and Australia’s COVIDSafe.
Remaining as Private as Possible
Multiple fake apps have already been detected during the pandemic, that’s why end-users should only install contact-tracing COVID-19 applications from official app stores since they only allow authorized government agencies to publish such apps.
However, it is still up to the developers of the applications to comply with standards by implementing them in a secure manner.