Cybercrime Africa
Awareness and Training Are Key in Defending Your Company from Blended Cyber-Threats
Image sourced from Finance Times. While blended cybersecurity threats are not new, they are fairly sophisticated and multi-staged in nature, meaning that they are difficult to protect against and can pose a considerable threat to organisations’ IT environments. A blended threat typically uses and exploits multiple vulnerabilities in an attack chain, says Brian Pinnock, Senior Director of Sales Engineering (EMEA) at Mimecast, adding that the severity of a blended threat will depend on the specific vulnerabilities that are targeted. “For example, a threat actor or cybercriminal will launch a phishing campaign against an organisation by sending emails with infected links that redirect to malicious websites. When a user clicks on these links, they could download a piece of malware like a Troja...
Cyber Threats on the Rise in Mining & Manufacturing Industries
Image sourced from Software ONE. Increasingly companies are looking to adopt smart technologies to optimise production and decision-making in order to create businesses of the future. However, as reliance on autonomous and digital technology grows, so too does the risk of cyber-attacks. As technologies become more interconnected, the potential cybersecurity threats and attack vectors are growing. The consequences of these threats can be severe, resulting in production and revenue losses, regulatory fines, reputational damage, as well as the shutdown of critical infrastructures. This has been further compounded by the complexities and uptake of smart systems that use advanced technologies such as machine learning and the Internet of Things (IoT). Mining, Manufacturing Under Threat Termed ‘S...
Broken Endpoints in Your Organisation’s Cybersecurity: The Role of Superior Endpoint Detection
Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited. Networks Unlimited is applying a ‘broken window, broken business’ principle when looking at an organisation’s internal cybersecurity posture, in order to have a positive effect on its business processes. The moral of the ‘broken window’ story, which has been studied by psychologists, is that once a window in a building is broken, people then feel that they are able to damage the property even further, and ultimately loot and steal from it, with impunity. “When we put this into a cybersecurity context,” says Stefan van de Giessen, General Manager: Cybersecurity at Networks Unlimited, “this means, in essence, making sure that you have no ‘broken windows’ or gaps in your security through which uninvited elements coul...
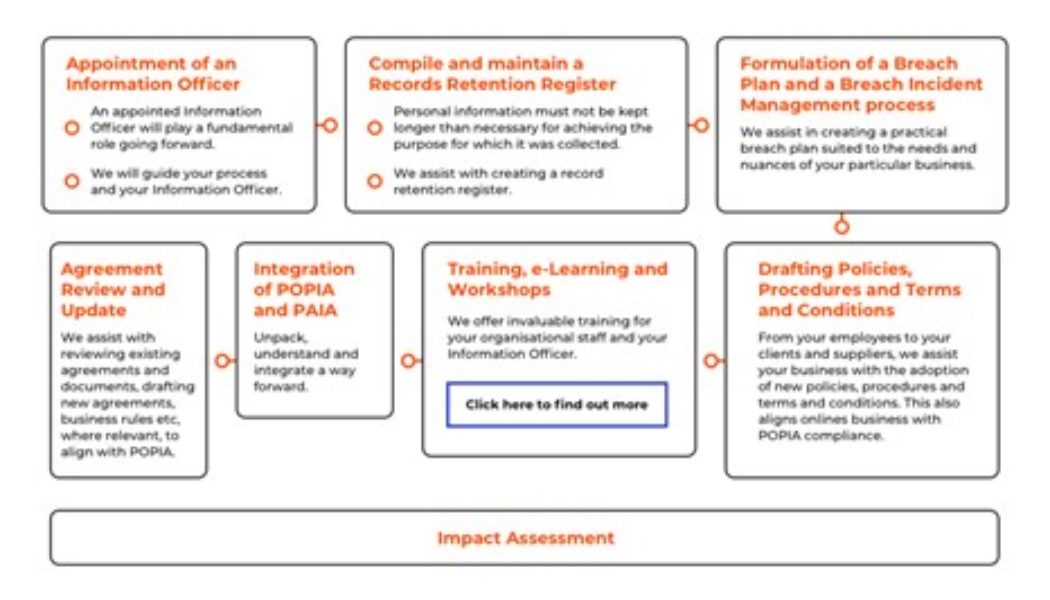
What is POPIA and What Does it Mean for Cybersecurity
With an inundation of information from all angles regarding The Protection of Personal Information Act (POPIA), and the 1 July commencement date quickly approaching, organisations could be forgiven for feeling more than a little overwhelmed. Emmanuel Tzingakis, Technical Lead for Trend Micro Sub-Saharan Africa, contemplates how POPIA can assist organisations to secure their data and be better enabled to handle any potential cyber threats. What is POPIA? With personal information becoming a hot commodity on the dark web it is critical to understand exactly how to protect data from cybercriminals. A recent global survey revealed that 79% of organisations experienced disruptions, financial loss or other setbacks due to a lack of cyber preparedness in 2020. As work from home strateg...