cybercrime
Chainalysis exec touts blockchain analysis to Senate homeland security committee
The collection and processing of information was a major theme at the United States Senate Committee on Homeland Security and Governmental Affairs (HSGAC) hearing titled, “Rising Threats: Ransomware Attacks and Ransom Payments Enabled by Cryptocurrency” on Tuesday. The committee hosted a panel of private-sector experts who discussed the problem of ransomware attacks and the challenges of collecting and using the information necessary to fight them. Committee chair Gary Peters of Michigan, who introduced the Strengthening American Cybersecurity Act in February, said the government lacks sufficient data even to understand the scope of the threat posed by ransomware attacks. Attackers almost exclusively ask for payment in cryptocurrency, he added. Several figures were trotted out to qua...
How the Russia-Ukraine War Could Affect Cybercrime
Image sourced from Packetlabs. Russia’s war on Ukraine and its increasingly isolated internet environment could drive Russian cybercriminals to think outside the box and launch new forms of cyber attacks. This is according to Nclose’s Co-Founder & Technical Director, Martin Potgieter, who says speculation and concern is mounting around the world, over what Russia’s cyber crime syndicates’ next moves will be. “Currently, the cybercrime focus appears to be predominantly between Russia and Ukraine cybercrime groups and governments. While this is strictly speaking cyber warfare, it could quickly spread elsewhere. “What we are seeing is that a few of these cybercrime groups are either taking sides or imploding amongst themselves due to their Eastern European links with one another,” says Po...
Ransomware Attacks on Healthcare Organizations Increased 94%, According to Sophos
Image sourced from Alpine Security. Sophos, a global leader in next-generation cybersecurity, has published a new sectoral survey report, “The State of Ransomware in Healthcare 2022.” The findings reveal a 94% increase in ransomware attacks on the organizations surveyed in this sector. In 2021, 66% of healthcare organizations were hit; 34% were hit the previous year. The silver lining, however, is that healthcare organizations are getting better at dealing with the aftermath of ransomware attacks, according to the survey data. The report shows that 99% of those healthcare organizations hit by ransomware got at least some their data back after cybercriminals encrypted it during the attacks. Additional ransomware findings for the healthcare sector include: Healthcare organizations had the se...
How to Stop the Costliest Internet Scams
Image sourced from isnews.stir.ac.uk According to Steve Flynn, Sales and Marketing Director at ESET Southern Africa, it’s long past time organisations get a handle on business email compromise scams which generated more losses for victims in 2021 than any other type of cybercrime. While ransomware, hacking, API hacks, and all the other cybersecurity threats make headlines, it’s worth remembering that the costliest internet scam is still business email compromises, according to the latest FBI Internet Crime Report. Among the complaints received by the FBI in 2021, ransomware, business e-mail compromise (BEC) schemes, and the criminal use of cryptocurrency are among the top incidents reported. Technology-based systems are under attack, and they cost organisations around the world billions in...
Crypto mixer sanctioned by US Treasury for role in Axie Infinity hack
The United States Treasury Department Office of Foreign Assets Control (OFAC) announced Friday that it was sanctioning cryptocurrency mixer Blender.io for its role in laundering proceeds from the hacking of Axie Infinity’s Ronin Bridge. North Korean state-sponsored hackers Lazarus Group have been identified as the perpetrators of the attack. Treasury Under Secretary for Terrorism and Financial Intelligence Brian E. Nelson said in a statement: “Today, for the first time ever, Treasury is sanctioning a virtual currency mixer. […] We are taking action against illicit financial activity by the DPRK and will not allow state-sponsored thievery and its money-laundering enablers to go unanswered.” Under the sanctions, all Blender.io property in the United States or in the possession of...
Omnis Security from NETSCOUT: Protect Your Network from the Threats You Can’t See
On 09 December 2021, the world was alerted to the Log4j vulnerability [CVE-2021-44228 aka Log4Shell]. It is likely that threat actors already knew about the vulnerability before this date, says Tom Bienkowski, NETSCOUT Product Marketing Director, because it’s been reported that the vulnerability had been exposed much earlier in Minecraft chat forums. How does Log4j work – and what lessons does it bring? Log4j, which is open-source software provided by the Apache Software Foundation, records errors and routine system operations and sends diagnostic messages about them to system administrators and users. A common example of Log4j is when a user types in or clicks on a bad weblink and they receive a 404 error message. The web server running the domain of the attempted weblink sends a message ...
North Korean Lazarus Group allegedly behind Ronin Bridge hack
The United States Treasury Department Office of Foreign Assets Control Specially Designated Nationals and Blocked Persons (SDN) list was updated Thursday to reflect the possibility that North Korean cyber-criminal Lazarus Group was behind last month’s hack of the Ronin Bridge, in which over 173,600 Ether (ETH) and 25.5 million USD Coin (USDC) was taken, Chainalysis announced by Twitter. The information was also confirmed by Ronin. The hack, which took place on March 23, was worth over $600 million at the time. Discovered several days after the fact, it is one of the biggest robberies of its kind in history. The coin came from the play-to-earn role-playing game Axie Infinity developed by the Vietnamese studio Sky Mavis. The game’s developers have raised over $150 milli...
How Emails Can Cause Cybersecurity Vulnerabilities in Your Organisation
Sourced from International IDEA Since the start of the pandemic, many businesses have shifted to remote work. Cybercriminals saw the opportunity to target businesses’ remote users leaving unprepared businesses vulnerable to cyberattacks. Phishing attacks have become one of the most prominent data security problems for a number of businesses in South Africa. “Remote working increased organisation’s reliance on email, creating the perfect conditions for email fraud and phishing,” says Riaan de Villiers, Business Analyst at LAWtrust Information Security. In the Mimecast State of Email Security 2020 study, businesses in South Africa reported a 53% increase in phishing attempts and a 46% increase in incidences of impersonation fraud compared to previous years. Email is a common channel used for...
The Challenges in Getting Internet Access to All South Africans
South Africa is on a drive to connect its citizens to the Internet. In November 2021, the Minister of Communications and Digital Technologies Khumbudzo Ntshavheni announced that the government was considering a programme to bring internet access to all South Africans within the next 24 months. Attempting to bridge the country’s digital divide, the programme would not only enable access to online services but also provide opportunities for a digitally-driven economy. The proposed programme indicates South Africa’s determination to embrace digital transformation. Never before has Internet connectivity been so paramount to the expansion and development of economic activity, especially in the age of wide-reaching digital services. But what does broad Internet access look like locally, and what...
Why Women Are Underrepresented in Cybersecurity
Sourced from Women in Tech Africa. One of the industries struggling with significant bias and gender stereotypes is cybersecurity. This field plays an increasingly crucial role in our digital world and, as a result, offers many fulfilling career paths and opportunities. However, there are still significant barriers and misperceptions driving the belief that a career in cybersecurity is not for women. While women have been disproportionately impacted by pandemic-driven unemployment (for example, one in four women reported job loss due to a lack of childcare—twice the rate of men), the technology sector was less affected. This was mainly due to their being better prepared to pivot to remote work and flexible work models. As a result, according to a report by Deloitte Global, l...
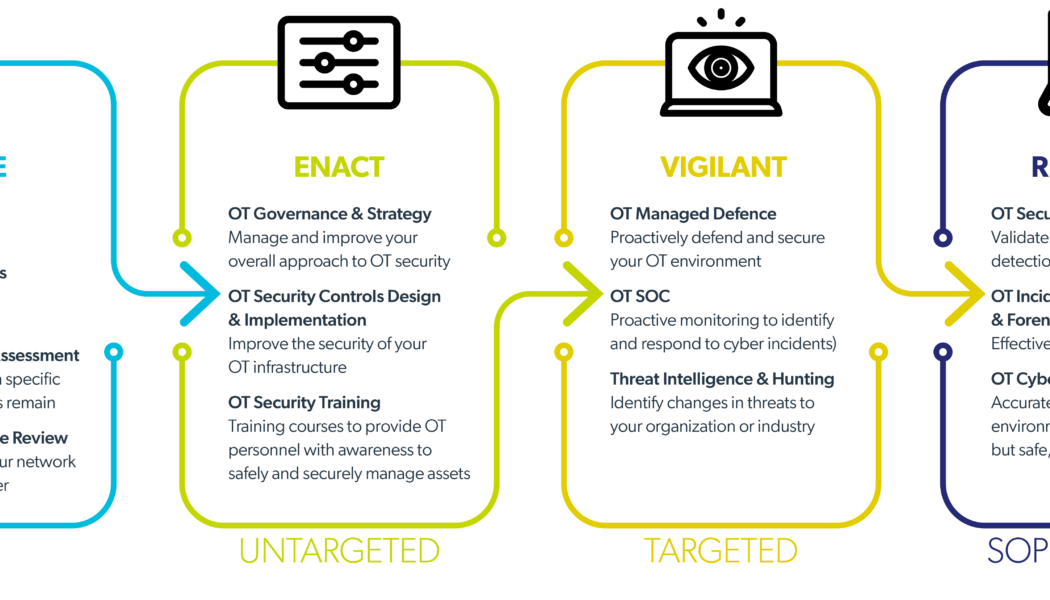
OT Security – Everything You Need To Know
Image sourced from Twitter: @SmartIndustryUS Most enterprises know that cyberattacks in the information security realm are continuously growing in sophistication, severity and number. However, up until now, many organisations that run plants, factories, pipelines and other infrastructure have paid less attention to the threats they face in the realm of operational technology (OT). Recent global, OT-focused cyberattacks highlight why South African utilities, manufacturers, oil & gas companies and other organisations that run industrial infrastructure would be wise to take note of the growing range of cyber threats faced by their OT systems and infrastructures. In one example, an intruder breached a water treatment plant in Florida in the US. The attacker briefly increased the quantity o...