Fortinet Security
Why Ransomware is the Greatest Threat to Your Organisation
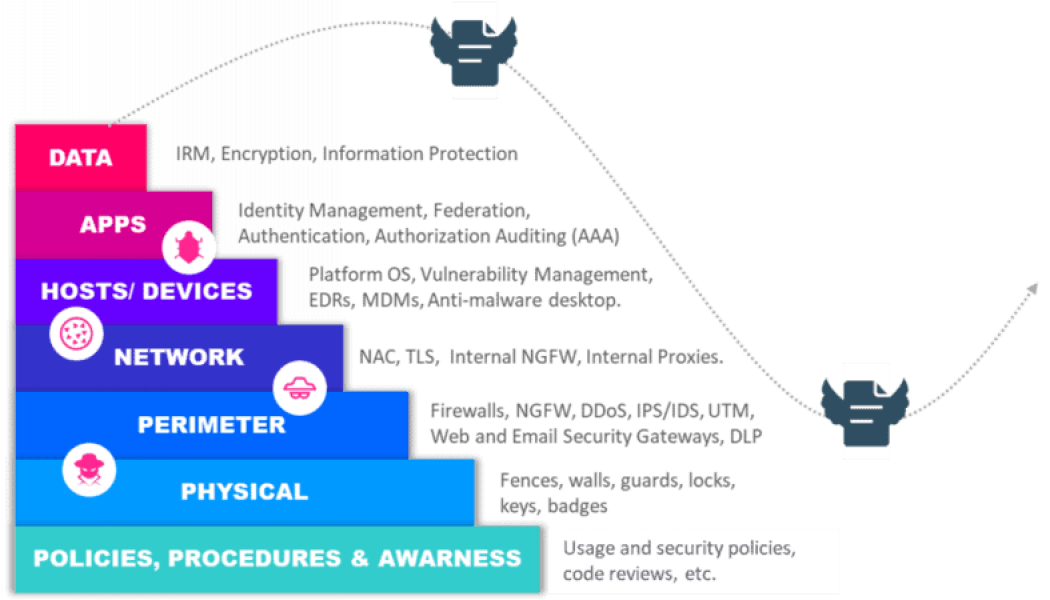
Ransomware is getting nastier and more expensive all the time and it has affected almost every industry and geography. No one is immune from the threat. In a global ransomware survey conducted by Fortinet, 67% of organizations report suffering a ransomware attack. Even worse, almost half said they had been targeted more than once, and nearly one in six said they had been attacked three or more times. Renee Tarun, Deputy CISO/ Vice President Information Security, Fortinet Inc. The US Treasury’s Financial Crimes Enforcement Network (FinCEN) reported that organizations paid out almost $600 million in ransomware in the first half of 2021, which puts the US on track to surpass the combined payouts of the previous decade in a single year. Last year’s attacks on the suppl...
FirstNet Technology Services Broadens its Security Offering with EDR Solution from Fortinet
Image by Darwin Laganzon, Pixabay. FirstNet Technology Services, a First Technology Group company, has broadened its security portfolio offering to include endpoint detection and response (EDR). As a long-time Fortinet partner, FortiEDR was the natural choice. This is according to Dave Campbell, Product Manager: Cloud Services at FirstNet, who explains, “FirstNet holds an Advanced Level partner status with Fortinet. Our cloud and security services are underpinned by a range of Fortinet products, with the use of solutions including FortiGate, FortiAnalyzer, FortiManager, FortiEDR, and FortiToken, which makes the FirstNet and Fortinet partnership a compelling offer for our customers.” “This experience has made us one of the top Fortinet partners in South Africa with a wealth of technical and...
iOCO Offers Africa-Focused SD-WAN Solution to IT Landscape
Brett van Rensburg, Sales Director for iOCO’s Compute Division After a year-long due diligence process, EOH, a JSE-listed technology services firm, through its IT services company, iOCO, has chosen to extend its partnership with Fortinet, a global leader in broad, integrated and automated cybersecurity solutions, in order to offer its software-defined wide-area networking (SD-WAN) solution to the southern African market. As explained by Fortinet, an SD-WAN solution connects users to any application wherever it resides, from the data centre to the cloud. SD-WAN intelligently determines which path best meets the ideal performance needs for a specific application. It then routes the traffic through to the best WAN path, whereas traditional WAN architectures only have the ability t...