Lists
How one point from five key games killed Fulham’s hopes of survival
Following a 2-0 defeat at home to Burnley, Fulham’s relegation from the Premier League was confirmed. The euphoria of August’s play-off final victory over local rivals Brentford seems like a distant memory, having sat in the relegation zone for all but four weeks of the season. Their failure to convert draws into wins has cost them dearly. They have the joint-fewest victories in the league this season with five, while only Brighton & Hove Albion can outdo their 12 draws. Here are five crucial games in Fulham’s season. Fulham 0-3 Aston Villa Grealish strikes early to give Fulham the lead It was a worrying start for Scott Parker’s side, who had lost their opening two games against Arsenal and Leeds United, conceding seven goals in the process. Perhaps the last thing they needed was a vis...
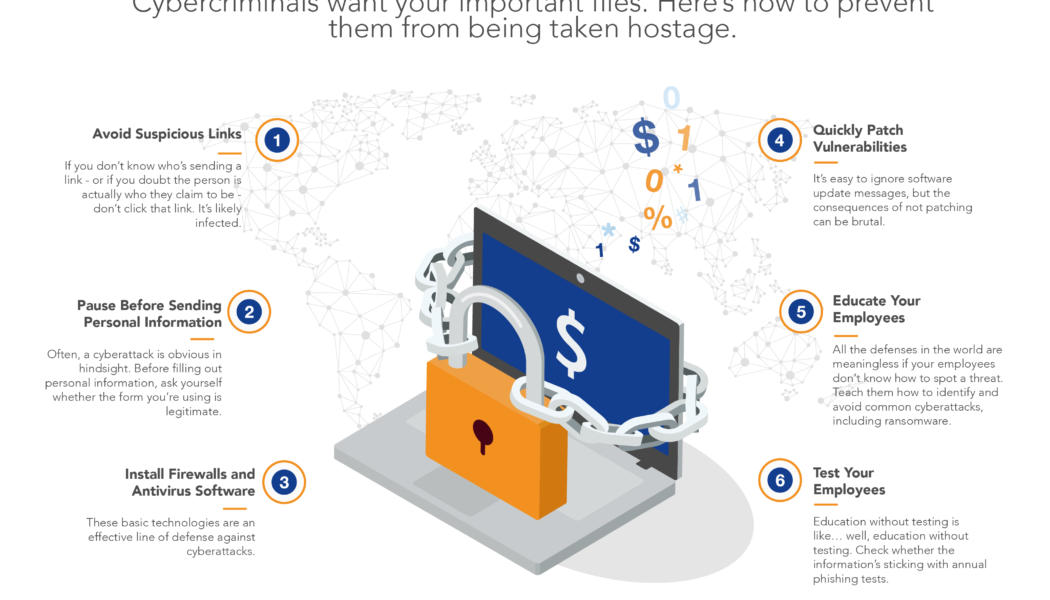
8 Ways to Protect Against Ransomware Attacks
Ransomware attack trends continue to evolve, and the current iterations are no exception. During the last year, malicious actors have attacked healthcare organisations, medical trials, schools, and shipping agencies. Considering the impact these modern attacks can have on organisations everywhere, no matter the industry, security professionals must always be ready to secure their systems, networks, and software in new ways. And according to a recent FortiGuard Labs global threat landscape report, ransomware remains a prolific threat that increased in 2020 and is set to more disruptive. With that in mind, here are eight ways to create a strong ransomware mitigation strategy: Continuously providing employees with updates on new social engineering attack methodologies so they know w...
7 Common Ways Cybercriminals Compromise Passwords
One of the most important parts of avoiding compromise is understanding how cybercriminals may attempt to gain access to your critical data, reveals Renee Tarun, VP of Information Security at Fortinet. He goes on to say that attack techniques continue to evolve and become more sophisticated, giving cybercriminals a vast toolkit to use to exploit users. Here are seven techniques to look out for: Social engineering attacks: Attacks such as phishing through emails and texts, where users are tricked into providing their credentials, clicking on malicious links or attachments, or going to malicious websites. Dictionary attacks: Attacker uses a list of common words, called the dictionary to try to gain access to passwords in anticipation that people have used common words or short pass...
5 Ways to Create the Perfect Remote Work Environment
Traditional work culture expectations are undergoing a paradigm shift, owing to the COVID-19 pandemic. According to a recent study, more than half of South Africans (53%) prefer the option of working from home at least once a week. Now more than ever, businesses need to foster a digital culture that encourages employees to engage and succeed regardless of where they work from. Here are five tips for building a strong and resourceful remote workforce: 1. Build a transparent communication system /* custom css */ .tdi_3_0e6.td-a-rec-img{ text-align: left; }.tdi_3_0e6.td-a-rec-img img{ margin: 0 auto 0 0; } Trust and transparency are the two major pillars of healthy team culture, and both thrive on communication. Ensure that every person in the team is aware of what’s going on in the company a...
6 Tips to Defend Against Ransomware Attacks
Over the last few years, the number of users encountering targeted ransomware – malware used to extort money from high-profile targets, such as corporations, government agencies, and municipal organisations – increased by 767%. With that in mind, here are 6 things you can do to defend against ransomware attacks: Assume you will be hit. Ransomware remains highly prevalent – no sector, country or organization size is immune from the risk. It’s better to be prepared, but not hit, rather than the other way round. Make backups and keep a copy offline. Backups are the main method organizations surveyed used to recover their data after an attack. Opt for the industry-standard approach of 3:2:1 (three sets of backups, using two different media, one of which is kept offline). Deploy layered protect...
Top 7 Forex Trading Apps for 2021
Mobile phones these days aren’t merely for entertainment and conversations. It has also made a lot of things more convenient for many users, including trading. Trading via smartphones allows easier access to your account and more benefits any time of the day regardless of your location. Because of this, you can get more opportunities that will help you grow your money. In fact, because of this, you can indulge in the market 24/7. Apps can also have various features that will help you trade better and have a better experience depending on your needs. With such apps, you won’t need to analyze big overwhelming charts. You can also take advantage of trend indicators and oscillators. However, it’s so easy for beginners to know where to start as numerous forex trading apps appear left and right ...
10 Most Face-Melting Moments by Dinosaur Jr.’s J Mascis
<span class="localtime" data-ltformat="F j, Y | g:ia" data-lttime="2021-04-19T15:50:12+00:00“>April 19, 2021 | 11:50am ET Deep into their illustrious career, alternative rock heroes Dinosaur Jr. are set to release their 12th studio album, Sweep It into Space, on April 23rd. It’s a testament to the enduring consistency of the band’s singer, guitarist, and central force J Mascis. A gifted multi-instrumentalist, Mascis first established himself as the speed-demon drummer of Massachusetts hardcore band Deep Wound. From there, he’d form Dinosaur with fellow Deep Wound member Lou Barlow in 1984. Guided by Mascis’ twangy, pseudo-country vocals and an incendiary electric guitar assault, Dinosaur broke onto the scene something like the punk-rock version of Neil ...
7 Ways to Protect Organisations from Ransomware Attacks
Sourced from International IDEA Over the past few years, the methods cybercriminals use to distribute ransomware has changed dramatically. While a few years ago, they would spread encrypted files on a large scale, today, their ransomware attacks have become more focused. Now, fraudsters examine the target in detail and research each target, looking for additional leverage. In order to protect business data from ransomware attacks, experts at Kaspersky recommend these seven tips: Installing only applications obtained from reliable sources from official websites Always have fresh backup copies of your files, so you can replace them in case they are lost (e.g. due to malware or a broken device). Remember to store them, not only on the physical object but also in the cloud for greater reliabil...
5 Ways Cybercriminal Gangs Use Ransomware
Over the past few years, the methods cybercriminals use to distribute ransomware has changed dramatically. While a few years ago, they would spread encrypted files on a large scale, today, their ransomware attacks have become more focused. Now, fraudsters examine the target in detail and research each target, looking for additional leverage. Infamous ransomware gangs behave like fully-fledged online service providers, using traditional marketing techniques. And according to Kaspersky, Internet users can see five clear examples of this transformation by looking at Darkside ransomware gang: 1. Darkside actively establishes contact with the press On their website, there’s a semblance of a press centre set up to enable journalists to ask questions and receive first-hand information and learn a...
5 decisive games in Sheffield United’s season
Following a 1-0 defeat against Wolverhampton Wanderers, Sheffield United’s relegation from the Premier League was confirmed with six games remaining. It’s been a miserable campaign for the Blades, racking up just 14 points from 32 outings, scoring only 17 goals. To say they’ve been a shadow of the team they were last season is being generous. The departure of Chris Wilder, coupled with the loss of Premier League TV revenue, could have a lasting impact at Bramall Lane. Here are five games that defined Sheffield United’s season. Sheffield United 0-1 Leeds United Sheffield United conceded late on, making it three games without a point Having lost their opening two games against Wolverhampton Wanderers and Aston Villa without scoring a goal, a fixture against a newly-promoted Leeds United side...
Top 10 Most Imitated Companies in 2021 So Far
In a brand phishing attack, cybercriminals try to imitate the official website of a well-known brand by using a similar domain name or URL and web page design to the genuine site. The link to the fake website can be sent to target individuals by email or text message, a user can be redirected during web browsing, or it may be triggered by a fraudulent mobile application. The fake website often contains a form intended to steal users’ credentials, payment details or other personal information. Check Point’s new Brand Phishing Report reveals the most frequently imitated by criminals. Here are the Top 10 phishing brands in Q1 of 2021: /* custom css */ .tdi_3_657.td-a-rec-img{ text-align: left; }.tdi_3_657.td-a-rec-img img{ margin: 0 auto 0 0; } Microsoft (related to 39% of all brand...
3 Cybersecurity Challenges Triggered by COVID-19 Lockdown
The global COVID-19 pandemic disrupted the everyday operations of businesses and as a result, the cyber risk still remains a grave concern as many business practices have been compromised. The ZA Central Registry organisation, which is the administrator of South Africa’s .za domain name, recently warned that South Africa is a global target for international fraudsters and cybersecurity measures are more important now than ever before. “It is essential for businesses to be aware of the nature of these cybercrimes and technology countermeasures to protect their businesses, especially when considering the cybersecurity challenges that have occurred during lockdown”, says Riaan de Villiers, Cybersecurity Expert and Business Analyst at LAWtrust. Here’s a Quick Look at the Top 3 Cybersecurity Ch...