Security
Ransomware Attacks on Healthcare Organizations Increased 94%, According to Sophos
Image sourced from Alpine Security. Sophos, a global leader in next-generation cybersecurity, has published a new sectoral survey report, “The State of Ransomware in Healthcare 2022.” The findings reveal a 94% increase in ransomware attacks on the organizations surveyed in this sector. In 2021, 66% of healthcare organizations were hit; 34% were hit the previous year. The silver lining, however, is that healthcare organizations are getting better at dealing with the aftermath of ransomware attacks, according to the survey data. The report shows that 99% of those healthcare organizations hit by ransomware got at least some their data back after cybercriminals encrypted it during the attacks. Additional ransomware findings for the healthcare sector include: Healthcare organizations had the se...
Small Businesses in Kenya Face 47% Increase in Cyber Attacks
When a small business owner is faced with the responsibilities of production economics, financial reports, and marketing all at the same time, cybersecurity can often appear complicated and, at times, unnecessary. However, this disregard for IT security is being exploited by cybercriminals. Kaspersky researchers assessed the dynamics of attacks on small and medium-sized businesses between January and April 2022 and the same period in 2021, to identify which threats pose an increasing danger to entrepreneurs. In 2022, the number of Trojan-PSW (Password Stealing Ware) detections in Kenya increased by 16% when compared to the same period in 2021 – 12 639 detections in 2022 compared to 10 934 in 2021. Trojan-PSW is a malware that steals passwords, along with other account inform...
These Are the Cyber Dangers Still Faced by SA’s SMEs
Image sourced from Pixabay Internet security provider Kaspersky says that small to medium-sized enterprises (SMEs) and other small businesses in South Africa are still facing many threats from cyber criminals and threat actors. What’s worse is that many small business owners do not use or believe it important to use cybersecurity services to secure their businesses. As commerce is moving ever continually online, this disregard for IT security continues to be exploited by cybercriminals. Kaspersky researchers assessed the dynamics of attacks on small and medium-sized businesses between January and April 2022 and the same period in 2021, to identify which threats pose an increasing danger to entrepreneurs. Cyber Threats Still Being Faced by SMEs in South Africa: In 2022, the number of Trojan...
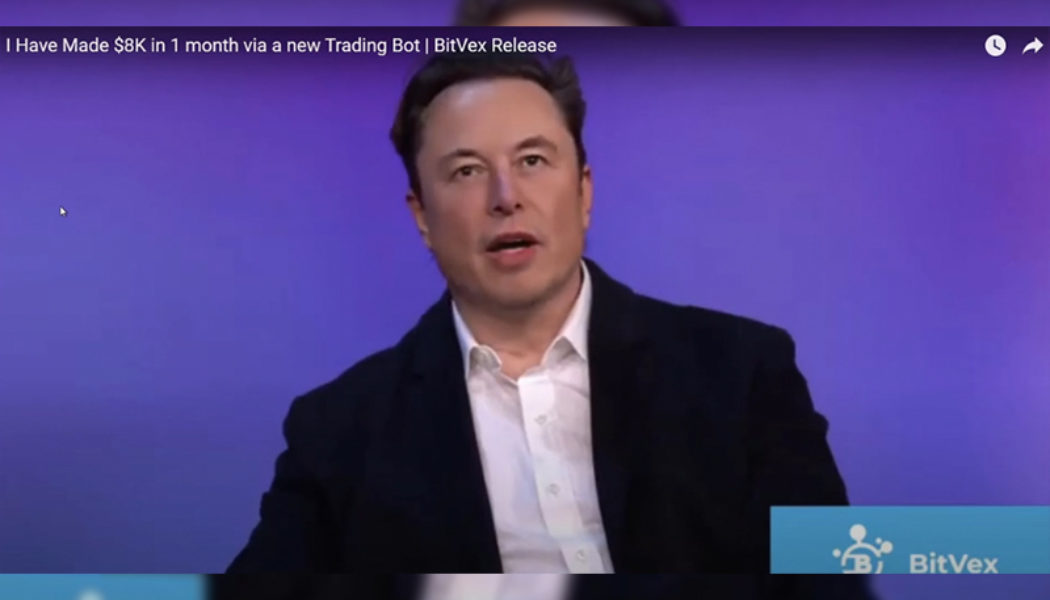
This is Not a Video of Elon Musk
A still from a deepfaked video of Elon Musk where he advertises a scam cryptocurrency. Scammers are using deepfake videos of Elon Musk in an attempt to trick people into handing over cryptocurrency, BleepingComputer reports. The scammers set up a phony cryptocurrency platform called “BitVex” that purports to be owned by Musk. The crooks then used hacked YouTube accounts to spread deepfaked videos of Musk and other people associated with cryptocurrency to promote the platform. “To use the BitVex platform, users must register an account at bitvex[.]org or bitvex[.]net to access the investment platform,” BleepingComputer says. “Once you log in, the site will display a dashboard where you can deposit various cryptocurrencies, select an investment plan, or withdraw your earnings. Like almo...
How Loadshedding Can Cause Cyber Security Risks
Image sourced from Forbes. Work-from-anywhere (WFA) model have greatly expanded in South Africa in recent weeks, as loadshedding forces remote workers to seek power from a multitude of sources, in malls and coffee shops, meaning they may be alternating between mobile phones, tablets and laptops across any number of potentially unsecured public Wi-Fi hotspots. This mobility increases the cyber security risks presented by all these devices that are often poorly secured to begin with. Smartphones, in particular, have become a critical part of the remote workforce toolkit. They are such an integral part of each person’s daily routine, people may regard them as trusted and safe. As a channel to your personal data, banking and accounts, and a link to your work and business data, smartphones...
How to Stop the Costliest Internet Scams
Image sourced from isnews.stir.ac.uk According to Steve Flynn, Sales and Marketing Director at ESET Southern Africa, it’s long past time organisations get a handle on business email compromise scams which generated more losses for victims in 2021 than any other type of cybercrime. While ransomware, hacking, API hacks, and all the other cybersecurity threats make headlines, it’s worth remembering that the costliest internet scam is still business email compromises, according to the latest FBI Internet Crime Report. Among the complaints received by the FBI in 2021, ransomware, business e-mail compromise (BEC) schemes, and the criminal use of cryptocurrency are among the top incidents reported. Technology-based systems are under attack, and they cost organisations around the world billions in...
Lacking Visibility: today’s biggest cybersecurity threat (and how to fix it)
Do you know the condition of your cybersecurity estate right now? Most companies have a tenuous grasp on whether their cybersecurity products and services are working as expected. What is the status of your patching? Are the security services delivering what you pay for? Do you know what the gaps and blind spots are in your security coverage? Above all, how long does it take for you to learn those answers? Days? Weeks? Creating accurate security reports takes time because you rely on numerous independent and uncoordinated vendor products with individual agents and data standards. Information often has to be manually compiled and harmonised into a single report. Time and insight are precious commodities for cybersecurity. Information from last week is not very useful to your current threats...