Security
What every leader must know about cybersecurity
Digitization means every single company now is vulnerable to cyberattacks. Cybersecurity has now become a topical issue affecting enterprises and the bedrock of tomorrow’s intelligent business. For enterprises to succeed they have to invest in digital capabilities that are robust and supported by a cybersecurity strategy that is sophisticated enough to ward off any attacks. Join Shelt & IT News Africa for this informative panel discussion around the constant threats enterprises face and what leaders in the industry need to know about building winning cybersecurity strategies for your business that go far beyond avoiding this worst case scenario. This will be followed by a simulation of a hypothetical crisis where the panel gets to discuss and come up with possible solutions. Date: ...
Custom Device Management: The Road Ahead for Businesses That Need More Than a Smartphone
Modern-day Mobile Device Management (MDM) solutions offer much more than basic device management features. Today’s business world cannot imagine a day without technology. All global industrial sectors rely on smartphones and computers to drive communication, automation and accelerate business operations. While these smart devices have dominated the corporate world for long enough, businesses are now moving towards a much more personalized digital approach. The usage of simple smartphones, tablets or laptops is not enough, organizations today desire digital devices that are customized for their business needs. Custom Devices for Diverse Businesses Major sectors like healthcare, hospitality, retail, education and logistics have advanced towards custom-made devices to cater to their distincti...
Bitcoin network hash rate explodes to a new all-time high of 248.11 EH/s
The Bitcoin (BTC) network has recorded a new hash rate all-time high of 248.11M TH/s as of Feb. 12, 2022, further securing the decentralized ecosystem through a growing network of global BTC miners. The hash rate correlates to the computing power required by a miner’s computer equipment to confirm a transaction. The recent spike in BTC’s network hash rate ensures further security against attacks by deterring bad actors from confirming fraudulent transactions. Bitcoin hash rate over the past year. Source: YCharts As evidenced by the above screenshot, the network hash rate jumped 31.69% — from 188.40 EH/s to 248.11 EH/s — in just one day. Moreover, the Bitcoin network’s hash rate levels rose 54.33% over the past year. Bitcoin hash rate over the past one month. Source: YCharts Pre...
Lost Bitcoin may be a ‘donation,’ but is it hindering adoption?
Cryptocurrency custody solutions have become a big business over the last few years. Independent storage and security systems meant to hold large quantities of crypto on behalf of clients can bring in institutional capital and retail investors waiting on the sidelines simply because they remove a major fear: losing access to funds that become unrecoverable. Because of the decentralized nature of major blockchains like that of Bitcoin or Ethereum, whenever a user loses access to their wallet and doesn’t have a backup of their private keys, the funds within it cannot be recovered. There’s no central entity to turn to, and no one can control the blockchain to give anyone access back to their funds. Storing a private key can be challenging, as it needs to be kept away from bad actors, yet clos...
Robust data backup is a vital line of ransomware defence
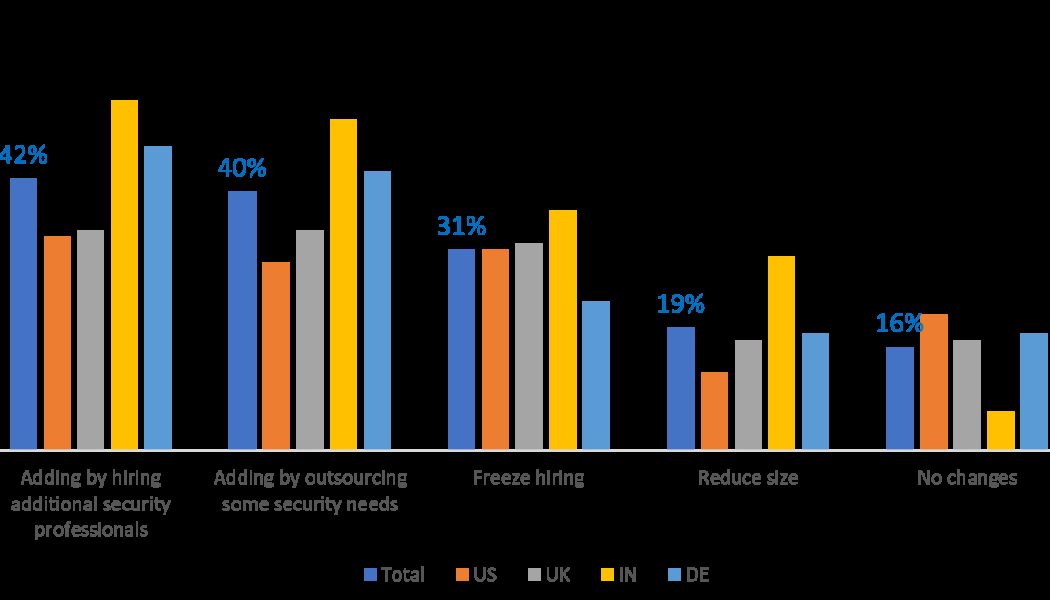
Image by Darwin Laganzon, Pixabay. It’s common knowledge that ransomware attacks are on the rise and organisations need to be realistic about what this means for their security. The number of entry points into IT systems that attackers can exploit has skyrocketed in recent years. According to the FBI, there has been a 300% rise in cybercrimes during the pandemic as more people log on to their work systems from home networks and personal devices. Ransomware isn’t going anywhere. Rising global connectivity, the recent rapid adoption of digital communication technologies, and remote working all create potential new ‘doors’ into IT systems. Growing technologies such as the cloud, 5G and the IoT means our connectivity will continue to multiply, meaning more doors and more opportunity for ransom...
The impact of the pandemic on cybersecurity
Ralph Berndt, Director of Sales at Syrex Even prior to the pandemic, organisations had begun putting in place elements to manage distributed employees whether that be through corporate remote desktop or virtual private networking (VPN) capabilities. However, this was not done at the scale and at a rate required to manage the disruption caused by COVID-19. Suddenly, companies had to deal with the influx of connectivity challenges that they needed to overcome for their employees to remain productive. Furthermore, support teams now had to manage providing access to critical systems, which were mainly hosted on-premises within the relative safety of their own corporate network. In many cases this resulted in companies having to implement more VPN licences to manage these additional external co...