Security
Kaspersky, Scuderia Ferrari extend partnership
Eugene Kaspersky (CEO Kaspersky) and Benedetto Vigna (CEO Ferrari) Leading global cybersecurity company, Kaspersky, has announced the continuation of its partnership contract with Scuderia Ferrari. In addition, the company joins a lineup of partners for the Ferrari Esports FDA team competing in the world Esports Series. The iconic partnership between Kaspersky and Scuderia Ferrari started in 2010 and since then has expanded year-on-year. United by shared values, including technological excellence, teamwork, and passion for innovation, the companies have been able to build a strong and proven relationship, including a technological partnership. Kaspersky provides Ferrari with world-class cybersecurity and data protection 24/7, at every point – from the company’s HQ factory in Maranello, Ita...
2022 Predictions: This could be a tough year for SA companies
Image sourced from Finance Times. While most of the world dealt with the impact and disruption of Year Two of the COVID-19 pandemic, cybercriminals expanded their activities with ambitious attacks on critical infrastructure. Armed with sophisticated and brute-force attack methods, threat actors continue to capitalise on the ongoing disruption of the pandemic and are leveraging the world’s shift to digital services to launch cyberattacks at an unprecedented scale. Can we expect a more cyber-secure world in 2022, or will cybercrime continue to disrupt our increasingly digital workplaces and lifestyles? Mimecast global experts weigh in on their predictions for the year ahead, which include: Social media & past breaches will come back to haunt us Peter Bauer, Mimecast CEO, predicts: “After...
ITC Secure and Cassava Technologies Announce Security Partnership
Image by Darwin Laganzon, Pixabay. ITC Secure (ITC), a leading advisory-led cyber security services company and a Microsoft Gold cyber security partner, and Cassava Technologies (CassavaTechnologies.com), the pan-African technology leader, announced today that they have entered into a Joint Venture (JV) to build and launch an extensive portfolio of cyber security services, powered by Microsoft Azure cloud technologies in Africa. Hardy Pemhiwa, the CEO of Cassava Technologies said: “Digital transformation in Africa is accelerating the adoption of cloud services which is creating an urgent need to better protect users and business-critical data. Cassava Technologies footprint covering more than 15 countries in Africa, we are well-positioned to meet the growing needs of businesses and individ...
Data centre risks: steps to protect the backbone of your business
Image sourced from Capacity Media. Data centres are the invisible but essential backbone of any modern business. Companies throughout the world have shifted to remote working, depending on cloud storage and cloud-based software as a service (SaaS) solution to ensure business continuity through the pandemic, and beyond. It’s anticipated that cloud solutions will account for more than 45% of IT spending by 2024, as corporations turn to these platforms to enjoy the benefits of lower costs, enhanced data analytics, and ways to collaborate more effectively. As much as these solutions are ‘cloud’ based, they’re hosted in massive terrestrial data centres, either owned by external providers, or by corporations themselves. They are vulnerable to various types of risks, including security threats su...
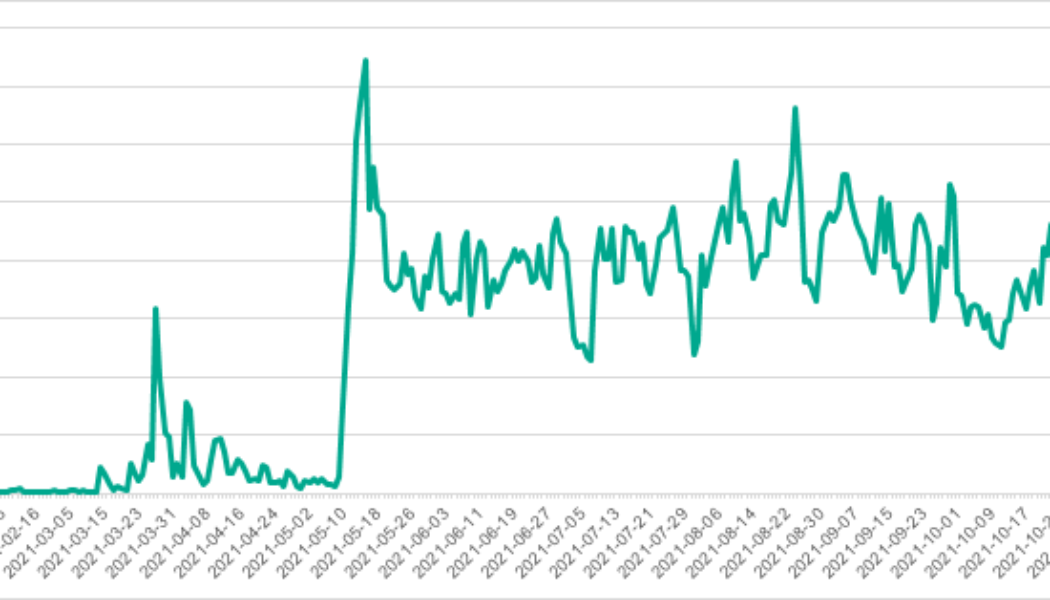
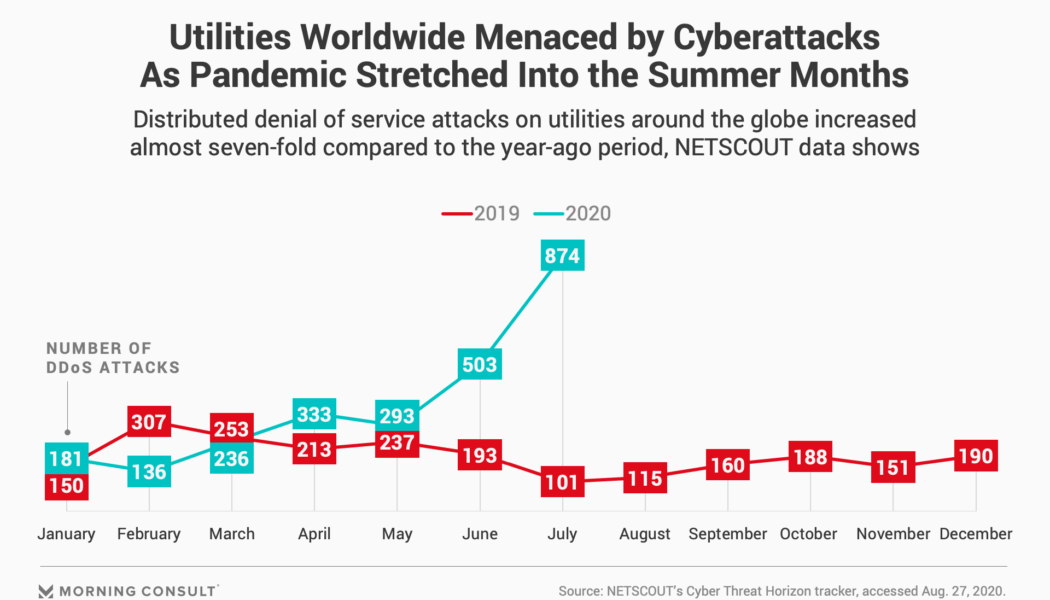
Kenya’s businesses are dealing with 1 400 cyber-attacks each week
This year has seen a 29% rise in cyberattacks against businesses across the world. In Africa, this growing threat is driven by an increase in users accessing the internet, creating a larger pool of targets for criminals, which is what we’ve witnessed in Kenya. The country’s connected population nearly reached 22 million users in January – a figure likely to have grown as pandemic lockdowns forced many business and government services online. With digital transformation being embraced across Kenya, how has cybercrime impacted local businesses? Statistics from the Check Point Research Threat Intelligence Report for Kenya highlight how widespread the problem is. Globally, the average number of weekly attacks experienced by organisations was 870. In comparison, Kenya’s busine...
How to Future Proof Your Email Security With Conditional Email Access
Sourced from My Smart Choice The contemporary world runs on rapid communication and while emphasizing corporate communications, the most reliable, cost-effective and quick means of formal communication is still considered email. But due to its popularity and widespread use, emails also happen to be the most targetted mediums for cyber attacks and spreading malware.One of the major concerns of enterprises is to safeguard their confidential data that contains their business secrets, plans of action, finance details and much more. Phishing attacks intending to hack into an enterprise’s systems and networks can expose the business’s vulnerabilities and lead to a loss of revenue and market share which makes it critical for a business to not take their corporate email security lightly.Why is cor...