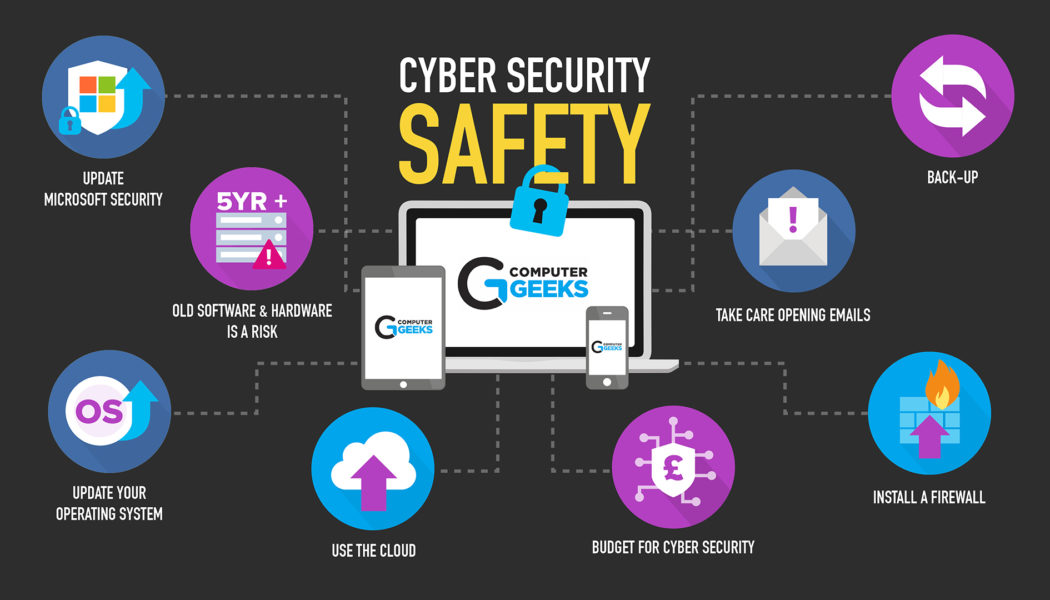
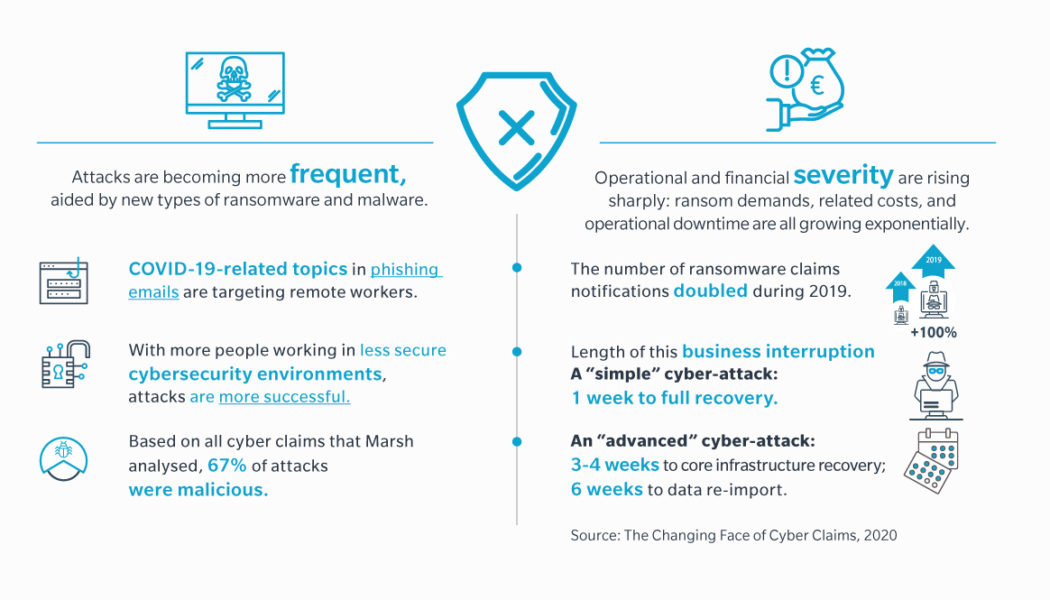
Security
1 in 4 People Use Fitness Devices – Is Your Tracking Data Secure from Hackers?
Image sourced from Reuters. A recent study by the virtual private network provider NordVPN revealed that 1 in 4 (24.6%) people use some kind of fitness or well-being device, such as a smartwatch, fitness tracker, etc. However, these devices may be tracking a lot more than your fitness activities, and 25% do nothing to protect them, which may pose a serious risk to people’s privacy. Among the data collected by fitness wearables and the mobile apps connected to them, there are basic activities such as steps, heart rate, the time you go to sleep or wake up, as well as your consumed calories, weight, or even running routes, which are all of great interest to stalkers or attackers. For example, Clario research has revealed that Strava collects 41.18% of users’ personal data, and MyFitnessPal — ...
How to Prevent Further CyberAttacks on Businesses & Government Departments
Image sourced from Finance Times. The recent ransomware attacks on the Department of Justice and Constitutional Development (DoJ) and the South African National Space Agency (Sansa) is a testament to the sophistication and aggressiveness of cybercrime in South Africa. In response to these attacks, organisations need to devise a preventative plan of action. “With South Africa having the third-highest number of cybercrime victims worldwide, and the biggest threat being ransomware, businesses are prone to being victims of ransomware traps unknowingly. In such cases, cyber-criminals pose as credible agencies with the intent of luring organisations to their demise,” says Maeson Maherry, CEO and co-founder of LAWtrust. What are Ransomware Attacks? Ransomware attacks are cyberattacks where a cybe...
How to Successfully Recover from a Ransomware Attack
Sourced from Kaspersky South Africa is an attractive target for cybercriminals for a number of reasons, and the last few years have seen a sharp rise in high-profile ransomware attacks. One of the key motivations driving this volume of attacks is the fact that data is a de facto currency and an extremely valuable commodity on the black market. While backup is a critical component of data protection, when this backup is also encrypted by malicious software, companies are often left with few options other than to pay the ransom. Therefore, an effective Cyber Recovery strategy, which enables businesses to get back up and running without having to give in to criminal demands, is the key. Ransomware on the Rise The rapid adoption of digital transformation, Artificial Intelligence (AI) and the I...
UN Calls on Nigeria, Others to Tighten Cybersecurity Regulations
Sourced from UN The International Telecommunications Union (ITU), the global telecommunications arm of the United Nations (UN) has called on the government of Nigeria, and other governments across Africa to strengthen their Internet safety regulations. Because of the COVID-19 pandemic, and general shift online, many African countries are now more exposed to cybersecurity threats than before, necessitating renewed efforts into protecting these spaces. According to the Guardian Nigeria, the UN noted that in Africa, many countries have seen a rise in reports of digital threats and other malicious cyber activities. The results include sabotaged public infrastructure, large-scale monetary theft from digital fraud, and national security breaches. The UN says that addressing these vulnerabilities...
The New DDoS ‘Normal’ is Not Normal in Any Way
Image sourced from Shutterstock. Threat actors will never turn down an opportunity for innovation, and the COVID-19 pandemic has provided an enormous such opportunity. We are seeing this quite clearly in the numbers coming through – and the new ‘normal’ around distributed denial of service (DDoS) attacks is not normal at all. So says Carole Hildebrand, Senior Strategic Marketing Writer at NETSCOUT, a leading global provider of service assurance, security and business analytics. Writing in a recent blog, she explains, “After an astonishingly active first quarter of DDoS attack activity, things calmed down a bit for the second quarter of 2021. Unfortunately, ‘calmed down’ is a relative term.” NETSCOUT decided to compare the numbers of DDoS attacks during the COVID-19 era of 2020 and 2021 thu...