Security
EA Games Struck by Massive Hack, FIFA 2021 Source Code on Dark Web
Sourced from Electronic Arts Inc. Gaming mega-publisher EA has been struck by a massive data hack. The hackers responsible have absconded with the source code for the hugely popular FIFA 21, as well as the source code for EA’s Frostbite Engine – the game-running shell and development tools behind FIFA as well as EA’s next big release Battlefield 2042. The source codes are reportedly currently being auctioned off in hacker forums on the dark web. The criminals behind the attack are only accepting offers from big-name members of the hacking community. Stolen Source Codes Source codes are the raw coding behind any application or programme. With a stolen source code and the right know-how, a user can duplicate a programme – for example, a video game – and do whatever they may wish to it. Usual...
Lagos governor asks security agencies to crush criminals
Lagos State Government has tightened the noose on criminal elements, as Governor Babajide Sanwo-Olu fortifies the armoury of the State Police Command with new hardware and gadgets. One hundred and fifty units of double cabin vehicles, 30 patrol saloon cars, four high-capacity troop carriers and two anti-riot water cannon vehicles are part of the crime-fighting equipment donated to the police, yesterday, by the Lagos Government to strengthen security responses across the state. President Muhammadu Buhari took inventory and inaugurated the security equipment before Governor Sanwo-Olu handed over the gears to the Inspector-General of Police (IG), Mr. Alkali Usman, for the use of Lagos Police Command. The equipment and gadgets were procured through the Lagos State Security Trust Fund (LSSTF) –...
President Buhari inaugurates police equipment in Lagos
President Muhammadu Buhari on Thursday inaugurated security equipment for the police and other security agencies in Lagos State. Governor Babajide Sanwo-Olu of Lagos officially handed over the patrol vehicles and various security equipment to the Inspector-General of Police, Usman Baba. The security equipment include 150 double cabin vehicles, 30 saloon patrol vehicles, 1000 ballistic vests, 1000 ballistic helmets, 1000 handheld police radios/walkie talkies and 100 security patrol bikes. Others are two Armored Personnel Carriers (APCs), four high capacity troop carriers, two anti-riot water cannon vehicles, office/command furniture and other ancillary support resources. Speaking at the handing over ceremony, Sanwo-Olu said that the state, local governments and corporate organisations contr...
Vulnerabilities in Windows and Chrome Used in Series of Highly Targetted Attacks
In April, Kaspersky experts discovered a number of highly targeted attacks against multiple companies utilising a previously undiscovered chain of Google Chrome and Microsoft Windows zero-day exploits. One of the exploits was used for remote code execution in the Chrome web browser, while the other was an elevation of privilege exploit fine-tuned to target the latest and most prominent builds of Windows 10. The latter exploits two vulnerabilities in the Microsoft Windows OS kernel: Information Disclosure vulnerability CVE-2021-31955 and Elevation of Privilege vulnerability CVE-2021-31956. Microsoft has patched both today as part of Patch Tuesday. Zero-Day Attacks Recent months have seen a wave of advanced threat activity exploiting zero-days on the internet. In mid-April, Kaspersky experts...
Police dispel report of armed Fulani invasion of Ekiti market
The Ekiti State Police Command has dispelled reports that armed Fulani bandits had stormed Ado Ekiti, the state capital. The state’s Commissioner of Police, Tunde Mobayo, said it is important to allay the fear that engulfed residents of the town when the news made the rounds on Wednesday. A report had trended online on Wednesday that a truck loaded with Hausa-Fulani men, all armed with AK-47 rifles and other weapons, had arrived at the Shasha market, along Ikere Road in Ado Ekiti. Mobayo, in a statement signed by the Command’s spokesman, ASP Sunday Abutu, and made available to reporters on Wednesday night, explained that the report was concocted by purveyors of fake news, and should be disregarded by residents of the town. The statement, entitled “No Armed Hausa/Fulani Invaded Shasha Marke...
Confidential Computing – Why Privacy Should be the Heart of Digital Experiences
Image sourced from Intel. In this past year, the consumer experience came to the forefront. As we faced various stages of lockdowns, we turned to online banking, seeing our doctors remotely, running our businesses using technology and socialising through a screen. Digital interactions became a part of our lives – ever-present and normalised as we navigated changes swept in by this pandemic. As our digital interaction became seamless and permeated through every aspect of our lives, privacy continued to be top of mind. We carried out our lives predominantly online – making many of us more vulnerable to fraudsters. As we navigated living our lives digitally, data theft dominated 2020 as the most common attack in the Middle East and Africa. Across the region, data theft and leaks accounted for...
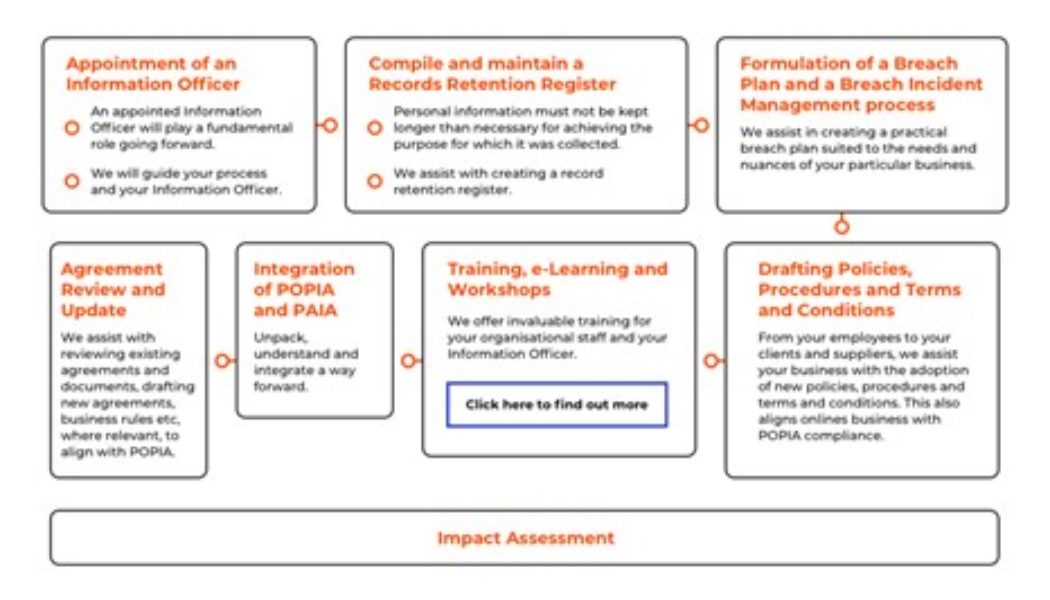
What is POPIA and What Does it Mean for Cybersecurity
With an inundation of information from all angles regarding The Protection of Personal Information Act (POPIA), and the 1 July commencement date quickly approaching, organisations could be forgiven for feeling more than a little overwhelmed. Emmanuel Tzingakis, Technical Lead for Trend Micro Sub-Saharan Africa, contemplates how POPIA can assist organisations to secure their data and be better enabled to handle any potential cyber threats. What is POPIA? With personal information becoming a hot commodity on the dark web it is critical to understand exactly how to protect data from cybercriminals. A recent global survey revealed that 79% of organisations experienced disruptions, financial loss or other setbacks due to a lack of cyber preparedness in 2020. As work from home strateg...