Security
Ethereum advances with standards for smart contract security audits
The Ethereum ecosystem continues to witness a flurry of activity that has individuals and organizations deploying token contracts, adding liquidity to pools and deploying smart contracts to support a wide range of business models. While notable, this growth has also been riddled with security exploits, leaving decentralized finance (DeFi) protocols vulnerable to hacks and scams. For instance, recent findings from crypto intelligence firm Chainalysis show that crypto-related hacks have increased by 58.3% from the beginning of the year through July 2022. The report further notes that $1.9 billion has been lost to hacks during this timeframe — a figure that doesn’t include the $190 million Nomad bridge hack that occurred on August 1, 2022. Although open source code may be beneficial for...
Cross-chains in the crosshairs: Hacks call for better defense mechanisms
2022 has been a lucrative year for hackers preying on the nascent Web3 and decentralized finance (DeFi) spaces, with more than $2 billion worth of cryptocurrency fleeced in several high-profile hacks to date. Cross-chain protocols have been particularly hard hit, with Axie Infinity’s $650 million Ronin Bridge hack accounting for a significant portion of stolen funds this year. The pillaging continued into the second half of 2022 as cross-chain platform Nomad saw $190 million drained from wallets. The Solana ecosystem was the next target, with hackers gaining access to the private keys of some 8000 wallets that resulted in $5 million worth of Solana (SOL) and Solana Program Library (SPL) tokens being pilfered. deBridge Finance managed to sidestep an attempted phishing attack on Monday, Aug....
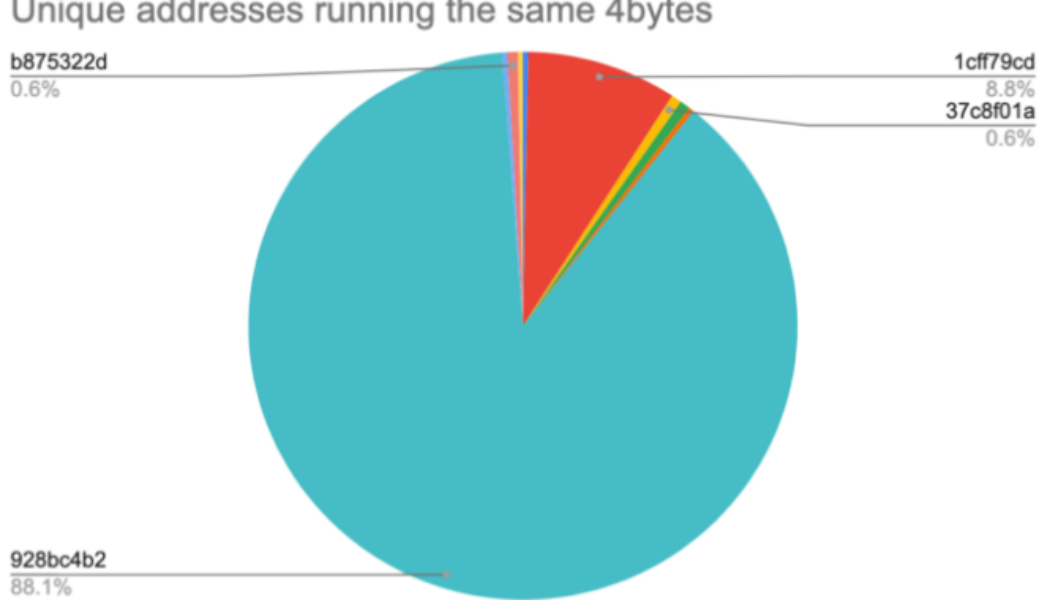
88% of Nomad Bridge exploiters were ‘copycats’ — Report
Close to 90% of addresses taking part in the $186 million Nomad Bridge hack last week have been identified as “copycats,” making off with a total of $88 million worth of tokens on Aug. 1, a new report has revealed. In an Aug. 10 Coinbase blog, authored by Peter Kacherginsky, Coinbase’s principal blockchain threat intelligence researcher, and Heidi Wilder, a senior associate of the special investigations team, the pair confirmed what many had suspected during the bridge hack on Aug. 1 — that once the initial hackers figured out how to extract funds, hundreds of “copycats” joined the party. Source: Coinbase According to the security researchers, the “copycat” method was a variation of the original exploit, which used a loophole in Nomad’s smart contract, allowing users to extract...
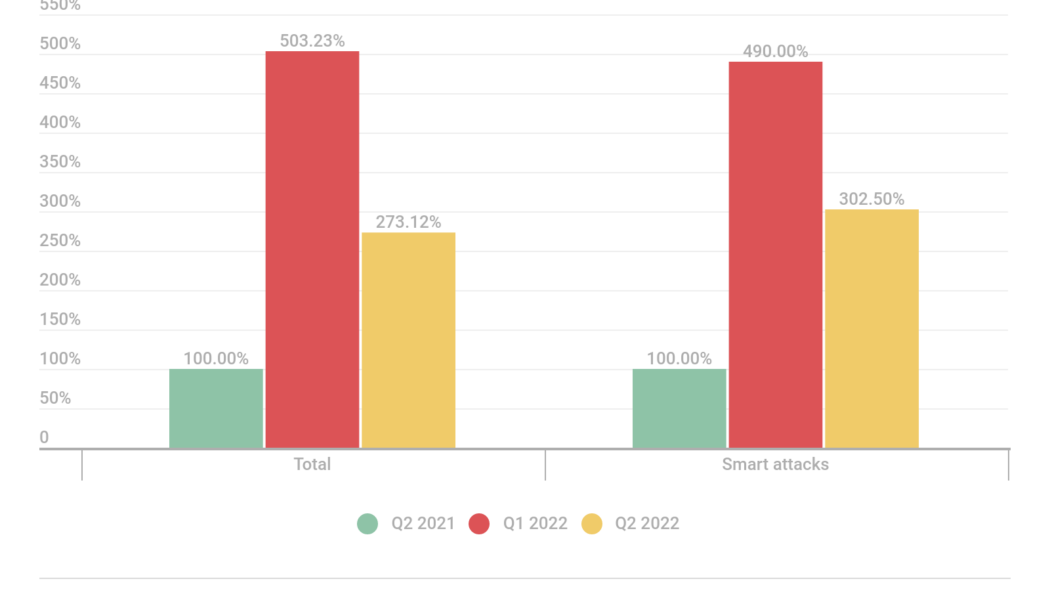
The Crypto Collapse & Rising DDoS Smart Attacks
Image sourced from Shutterstock. During Q2 2022, Distributed Denial of Service (DDoS) attacks reached a new level as the share of smart attacks and average duration saw steep increases. Compared to the previous year, the average duration of a DDoS attack rose 100 times, reaching 3,000 minutes. The share of smart attacks almost broke the four-year record, accounting for nearly 50% of the total. Experts also expect an increase in overall DDoS activity, especially with the recent collapse of cryptocurrency. These and other findings are part of a quarterly DDoS report issued by Kaspersky. A Distributed Denial of Service (DDoS) attack is designed to hinder the normal functioning of a website or crash it completely. During an attack (which usually targets government institutions, retail or ...
The worst places to keep your crypto wallet seed phrase
Under the mattress, in the seams of a piece of luggage or even rolled into a cigar, what are the worst and best ways for keeping a seed phrase safe? The key to unlocking and recovering cryptocurrency, a seed phrase, should be secured and safe. Especially now that prices are low and the crypto tourists have checked out, it might be time for a crypto security spring clean. Security starts with a seed phrase, sometimes called a recovery phrase. There’s no denying it: Bitcoin and the crypto space writ large are in the clutches of a bear market. Since Do Kwon’s Terra experiment went up in smoke, a crypto contagion has choked the most reputable of exchanges, causing many self-sovereignty advocates to chant, “not your keys, not your coins.” Indeed, hardly a day goes by that another “trusted...
Why the Healthcare Sector Must Prioritise Modern Data Protection
Image sourced from Healthcare Finance. The pandemic has put a significant strain on all industry sectors none more so than in healthcare where there was a need to adopt more data-driven planning and decision-making at lightning speed. At a time when expanding remote care, telemedicine, and m-health initiatives have become the order of the day, the spotlight has turned to the safeguarding of sensitive information at a scale comparable to the financial services sector. This is for good reason. According to the ‘Veeam Top Trends in Data Protection, Healthcare Edition 2022’ report, 76% of global healthcare organisations had at least one ransomware attack in the last year. This has contributed to an almost 5% increase in data protection budgets that include backup, business continuity, and disa...
Ethereum will outpace Visa with zkEVM Rollups, says Polygon co-founder
zkEVM Rollups, a new scaling solution for Ethereum, will allow the smart contract protocol to outpace Visa in terms of transaction throughput, said Polygon co-founder Mihailo Bjelic in a recent interview with Cointelegraph. Polygon recently claimed to be the first to implement a zkEVM scaling solution, which aims at reducing Ethereum’s transaction costs and improving its throughput. This layer-2 protocol can bundle together several transactions and then relay them to the Ethereum network as a single transaction. The solution, according to Bjelic, represents the Holy Grail of Web3 as it offers security, scalability and full compatibility with Ethereum, which means developers won’t have to learn a new programing language to work with it. “When you launch a scaling solution,...