Politics
Wazupnaija – Naija Entertainment blogs & Forums – Politics
This Nigerian Fintech Unicorn is Taking Egypt by Storm
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
Effective Data Backup Becomes Essential as Kenya is Rocked by Ransomware
In the wake of the COVID-19 pandemic, cybercrime, in particular, ransomware, has seen a massive increase across the globe. As a burgeoning economy in Africa, Kenya has become a growing target, with a new report from internet security group Kaspersky recording 32.8 million attacks in the first half of 2021. According to INTERPOL, increasing digital demand in the country, coupled with “a lack of cybersecurity policies and standards, exposes online services to major risks”. As digital transformation continues to gain traction in Kenya, data becomes increasingly important for business, and it needs to be effectively protected. Effective data backup and recovery are key to overcoming the potential threat of a ransomware attack. Connected, but vulnerable In Kenya, as in much of the world, the pa...
How the Secondary IT Market Became the Unsung Hero of the Pandemic
Kwirirai Rukowo, General Manager of Qrent. COVID-19 triggered an explosion of the global remote workforce and online learning, which created an extraordinary demand for new tech gear. It also forced the shutdown of chip-making facilities around the world and according to industry executives and analysts, returning supply chains to their pre-pandemic state will be a lengthy process. Demand has far exceeded supply, and for the last two years, we’ve seen a shortage and shipment delays of electronics such as TV’s, mobile phones, computers, cars and game consoles. According to leading technology research expert Gartner Inc., new restrictions and supply chain disruptions caused by the Omicron variant could further delay the market’s recovery. In a pessimistic scenario, Gartner believes that this...
Street Fighter 6 Announced by Capcom – Check Out Ryu’s New Look
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
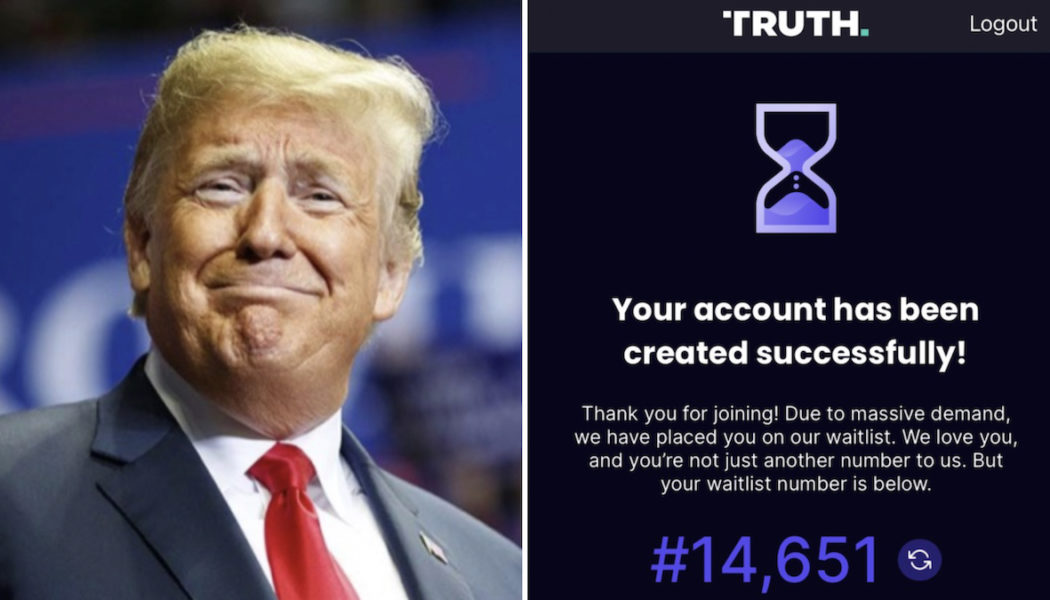
Trump’s Truth Social Comes to App Store, Doesn’t Work
Truth Social, the new social media platform from former President Donald Trump, launched today in Apple’s App Store and promptly failed to work. As Axios and others have reported, new users weren’t able to use the app, but instead were immediately added to a waitlist. “You’re not just another number to us,” the message reads, before assigning them a number. Some people were invited to be beta testers last week, and Trump-supporting congressional representatives like Madison Cawthorn (R-N.C.) and Marjorie Taylor Greene (R-Ga) were able to use Truth Social and report bugs. It’s unclear how long new users will stay on the waitlist, when it will come to Android and other platforms, or even how far the app has been developed. Advertisement Related Video Truth Social has been touted as a bastion...