Cybersecurity Tips
Unpacking Lessons from Ransomeware Attacks in 2021
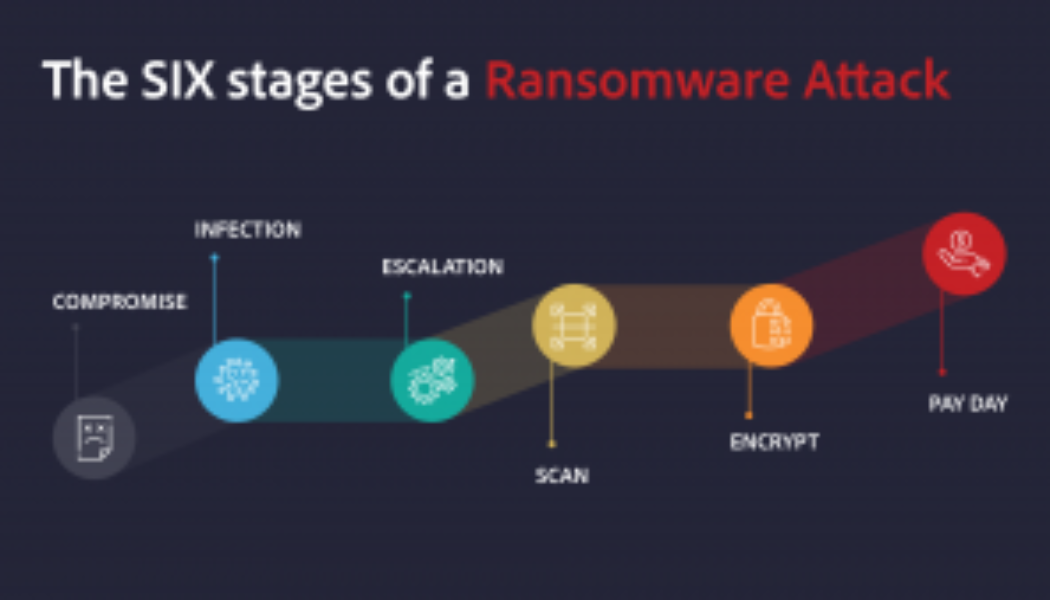
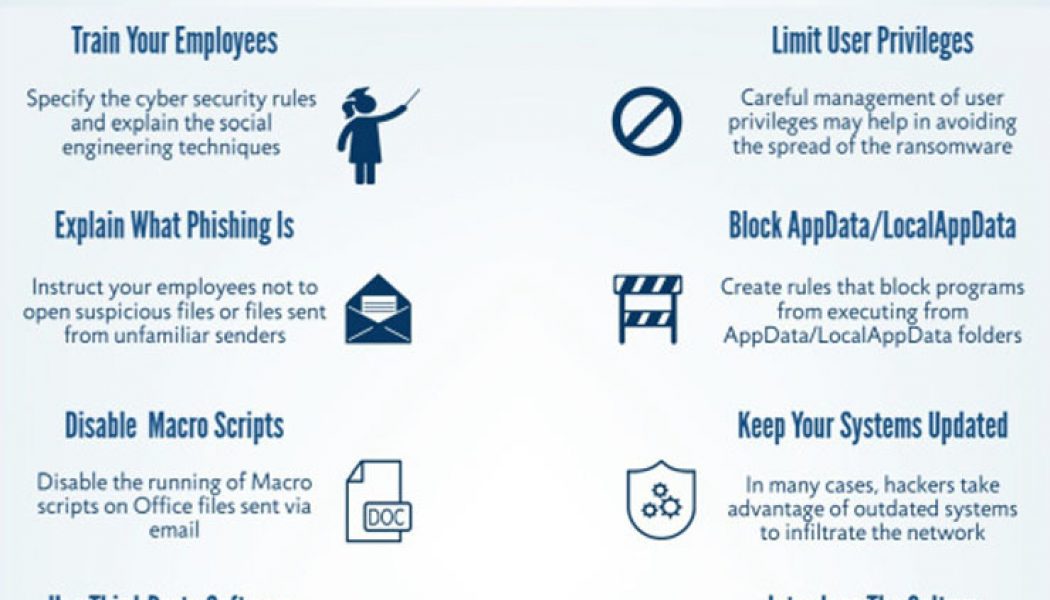
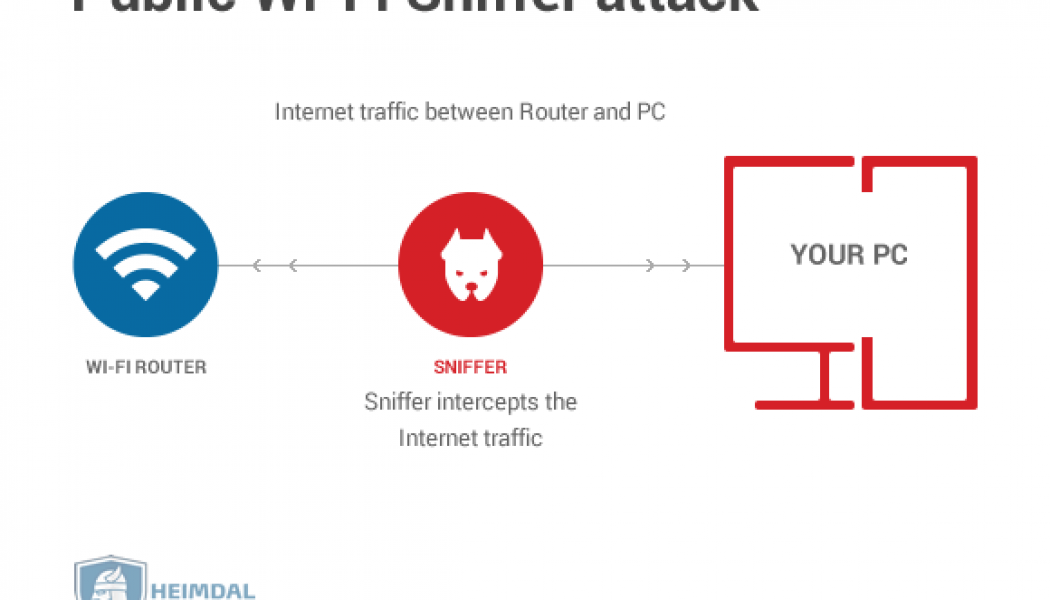
It’s nearly impossible to read the news without seeing at least one headline blaring about a breach, hack or attack. In the USA, the Colonial Pipeline experienced a Darkside ransomware attack that affected more than 10, 000 gas stations. Virgin Active was hit by a hack in early May 2021 and took weeks to re-establish its systems. Vastaamo, a platform that provided therapy to thousands of patients, lost its data to hackers thanks to an unexpected security flaw. The hackers sent ransom demands to patients – pay up, or your personal information is public knowledge. As Stephen Osler, Co-Founder and Business Development Director at Nclose, points out, the criminal networks and masterminds behind digital attacks are doing their jobs and have every motivation to do these jobs extremely well. “The...
Beware of this New SMS Phishing Scheme Spreading Worldwide
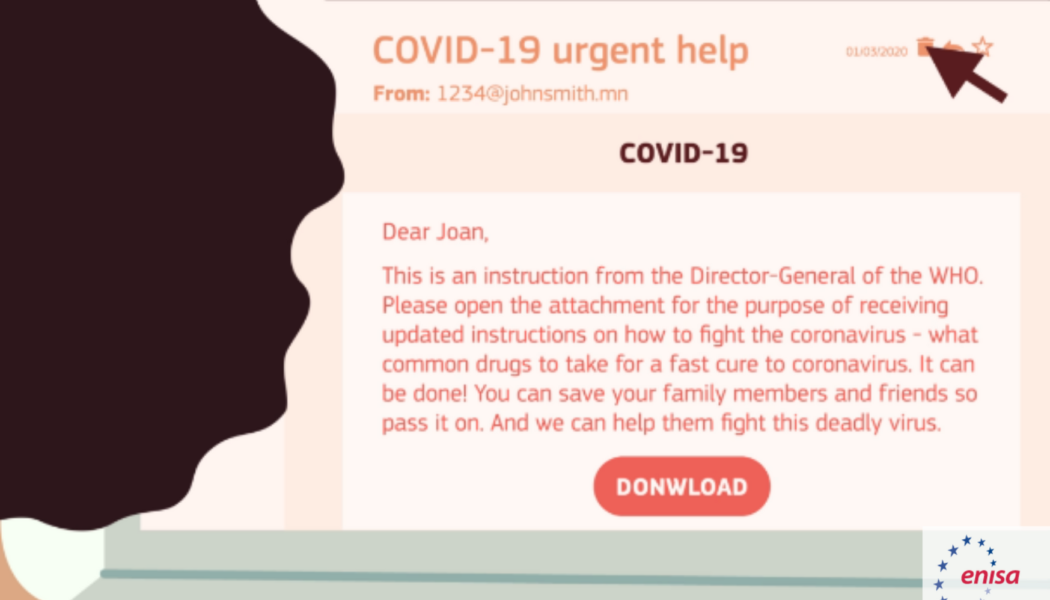
A new, and viral, phishing scheme has seen fraudsters putting mobile users’ financial information at risk, according to Kaspersky. The cybersecurity company revealed that attackers, typically under the guise of a postal service, request a small sum of money for the shipping costs of a package. Once a user clicks on an SMS authentication code for the money transfer, the device is compromised thereby enabling increasingly larger amounts of money to be stolen. “Because it is not a complex phishing attack, it has already gained traction in other parts of the world with fraudsters able to pose as virtually any service provider from prepaid electricity to airtime, naming just a few examples,” says Bethwel Opil, Enterprise Sales Manager at Kaspersky in Africa. Phishing, regardless of the scheme u...
Here’s How Many Mobile Users in Kenya and Nigeria are Affected by Stalkerware
Stalkerware affects one out of every 100 mobile users in Kenya and Nigeria, according to Kaspersky Research. The same report reveals that similar malware impacts every four out of 100 South Africans. “Even though these numbers might seem low, especially when it comes to stalkerware, it bears mentioning that this form of attack is focused on specific individuals,” says Lehan van den Heever, Enterprise Cyber Security Advisor for Kaspersky in Africa. “So, unlike general malware that is distributed on a massive scale, stalkerware is a more personal crime that has life and death consequences for the individual affected, for example, a perpetrator can track down their estranged partner with ill intentions, or human trafficking rings targeting children.” Amongst other things, stalkerware can enab...
What is Cyber Doxxing and How to Protect Against It
Since the beginning of internet errors, a lot of personal details is revealed. Publishing personal data online may be very dangerous. The internet is a pool where you will find all sorts of people including hackers, cyberbullies, and other people with defamatory intentions. Such people collect and publish personal information with a bad intention. When this is done, it is known as Doxxing. Doxxing comes from the word “documents” with the act of documenting another person’s information. Criminals dig up personal details of an individual who wants to remain anonymous and expose them to the public. The main aim is to harass or shame the person. Although details like email addresses, phone numbers, and social security numbers are available online, there are other details like pictures, financi...