hack
The 10 largest crypto hacks and exploits in 2022 saw $2.1B stolen
It’s been a turbulent year for the cryptocurrency industry — market prices have taken a huge dip, crypto giants have collapsed and billions have been stolen in crypto exploits and hacks. It was not even halfway through October when Chainalysis declared 2022 to be the “biggest year ever for hacking activity.” As of Dec. 29, the 10 largest exploits of 2022 have seen $2.1 billion stolen from crypto protocols. Below are those exploits and hacks, ranked from smallest to largest. 10: Beanstalk Farms exploit — $76M Stablecoin protocol Beanstalk Farms suffered a $76 million exploit on April 18 from an attacker using a flash loan to buy governance tokens. This was used to pass two proposals that inserted malicious smart contracts. The exploit was initially thought to have cost around $182 mil...
Gemini allegedly suffered data breach; 5.7 million emails leaked
Cryptocurrency exchange Gemini appears to have suffered a data breach on or before Dec. 13. According to documents obtained by Cointelegraph, hackers gained access to 5,701,649 lines of information pertaining to customers’ account numbers, email addresses and partial phone numbers. In the case of the latter, hackers apparently did not gain access to the full phone numbers, as certain numeric digits were obfuscated. The leaked database did not include sensitive personal information such as names, addresses and other Know Your Customer information. In addition, some emails were repeated in the document; thus, the number of customers affected is likely lower than the total rows of information. Gemini currently has 13 million active users. Security breaches in the Web3 industry, even if mild i...
Crypto scammers are using black market identities to avoid detection: CertiK
Crypto scammers have been accessing a “cheap and easy” black market of individuals willing to put their name and face on fraudulent projects — all for the low price of $8, blockchain security firm CertiK has uncovered. These individuals, described by CertiK as “Professional KYC actors” would, in some cases, voluntarily become the verified face of a crypto project, gaining trust in the crypto community prior to an “insider hack or exit scam.” Other uses of these KYC actors include using their identities to open up bank or exchange accounts on behalf of the bad actors. According to a Nov. 17 blog post, CertiK analysts were able to find over 20 underground marketplaces hosted on Telegram, Discord, mobile apps, and gig websites to recruit KYC actors for as low as $8 for simple “gigs” lik...
FTX hacker is now the 35th largest holder of ETH
The hacker that exploited the now-bankrupt FTX exchange last week made a tidy fortune that has propelled them to Ether (ETH) whale status. Just a day after the embattled FTX exchange filed for Chapter 11 bankruptcy, its wallets were drained for more than $663 million in various crypto assets, according to blockchain intelligence company Elliptic. Elliptic suspected $477 million of this was stolen, with a large chunk of those tokens being then converted into ETH, while $186 million worth of more than a hundred different tokens was believed to be moved into secure storage by FTX itself. As reported by Cointelegraph on Nov. 15, the attacker was still draining wallets four days later in what analysts called “on-chain spoofing.” According to blockchain security firm Beosin, the attacker has con...
White hat finds huge vulnerability in ETH to Arbitrum bridge: Wen max bounty?
A self-described white hat hacker has uncovered a “multi-million dollar vulnerability” in the bridge linking Ethereum and Arbitrum Nitro and received a 400 Ether (ETH) bounty for their find. Known as riptide on Twitter, the hacker described the exploit as the use of an initializing function to set their own bridge address, which would hijack all incoming ETH deposits from those trying to bridge funds from Ethereum to Arbitrum Nitro. Riptide explained the exploit in a Medium post on Sept. 20: “We could either selectively target large ETH deposits to remain undetected for a longer period of time, siphon up every single deposit that comes through the bridge, or wait and just front-run the next massive ETH deposit.” The hack could have potentially netted tens or even hundreds of millions worth...
Binance identifies KyberSwap hack suspects, involves law enforcement
Helping investigate a $265,000 hack on decentralized crypto exchange KyberSwap, crypto exchange Binance narrowed down two suspects that seem responsible for the attack. On Sept. 1, Kyber Network succumbed to a frontend exploit, allowing the attacker to make away with $265,000 worth of user funds from KyberSwap. While investigations were underway, KyberSwap offered a 10% bounty — of roughly $40,000 — to the hacker as means to remediate the situation. Parallelly, based on an independent investigation, Binance’s security team identified two suspects that may be responsible for orchestrating the virtual heist. Binance CEO Changpeng ‘CZ’ Zhao confirmed that the intel had been sent to the Kyber team. #Binance security team has identified two suspects for yesterday’s KyberSwap hack. W...
8 sneaky crypto scams on Twitter right now
Cybersecurity analyst Serpent has revealed his picks for the most dastardly crypto and nonfungible token (NFT) scams currently active on Twitter. The analyst, who has 253,400 followers on Twitter, is the founder of artificial intelligence and community-powered crypto threat mitigation system, Sentinel. In a 19-part thread posted on Aug. 21, Serpent outlined how scammers target inexperienced crypto users through the use of copycat websites, URLs, accounts, hacked verified accounts, fake projects, fake airdrops and plenty of malware. One of the more worrisome strategies comes amid a recent spate of crypto phishing scams and protocol hacks. Serpent explains that the Crypto Recovery Scam is used by bad actors to trick those who have recently lost funds to a widespread hack, stating: “Simply pu...
Solana wallets ‘compromised and abandoned’ as users warned of scam solutions
The cryptocurrency ecosystem has been rocked by a widespread exploit targeting Solana wallets that have been ongoing since Aug. 3. Phantom and Slope, two Solana-based wallet services, initially flagged the attack on their social media platforms, alongside a host of cryptocurrency influencers, blockchain analytic and security firms and victims of the hack as it continued to unfold. A handful of commentators noted that attackers had gained access to user private keys, as transactions were signed on the chain legitimately. Ava Labs CEO and founder Emin Gun Sirer estimated that more than 7,000 wallets had been affected, a number cited by various other individuals and firms online. As investigations begin to unpack the root cause that allowed an attacker to pillage thousands of wallets, affecte...
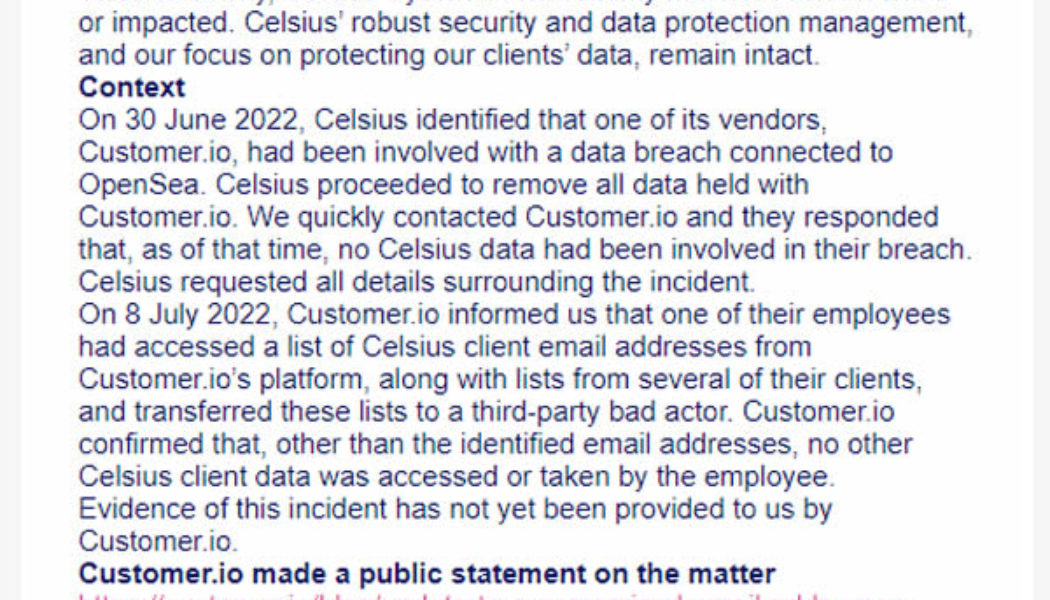
Phishing risks escalate as Celsius confirms client emails leaked
Celsius depositors should be on the lookout for phishing scams after the company revealed some of its customer data has been leaked in a third-party data breach. On July 26, Celsius sent an email to its customers informing them that a list of their emails had been leaked by an employee of one of its business data management and messaging vendors. According to Celsius, the breach came from an engineer at the Customer.io messaging platform who leaked the data to a third-party bad actor. “We were recently informed by our vendor Customer.io that one of their employees accessed a list of Celsius client email addresses,” said Celsius in its email to customers. The data breach is part of the same incursion that leaked OpenSea customer email addresses in June. Announcement from Celsius: “We ...
Solana and Ethereum smart contract audits, explained
As you might expect, this depends on how complex a smart contract is. According to Hacken, this can extend to $500,000 for larger projects where there are more lines of code — not least because of the additional engineering hours it’ll take. The company argues these costs pale into comparison with the economic damage that a smart contract vulnerability can bring. Hacken cites data showing that, in 2021, 80% of the incidents affecting decentralized applications related to smart contracts — with losses hitting $6.9 billion. Breaking this down even further, and we can see that the average cost per project stands at $47 million. Somehow, $500,000 looks a lot less expensive now. Overall, 60% of its clients have been based on Ethereum so far in 2022. And here&...
Targeted phishing scam nets $438K in crypto and NFTs from hacked Beeple account
Digital artist and popular non-fungible token (NFT) creator Mike Winkelmann, more commonly known as Beeple, had his Twitter account hacked on Sunday, May 22 as part of a phishing scam. Harry Denley, a Security Analyst at MetaMask, alerted users that Beeple’s tweets at the time containing a link to a raffle of a Louis Vuitton NFT collaboration were in fact a phishing scam that would drain the crypto out of users’ wallets if clicked. ⚠️ Beeple’s Twitter account has been compromised (ATO) to post a phishing website to steal funds. 0x7b69c4f2ACF77300025E49DbDbB65B068b2Fda7D0xF305F6073CFa24f05FF15CA5b387DD91f871b983 pic.twitter.com/0MPNwOPlEu — harry.eth (whg.eth) (@sniko_) May 22, 2022 The scammers were likely looking to capitalize on a real recent collaboration betwe...
Monero community concerned as leading mining pool nears 51% of ecosystem’s total hash rate
On Tuesday, privacy coin Monero (XMR) mining pool MineXMR’s hash rate surpassed over 1.4 GH/s, accounting for 44% of the hash rate of the XMR network. MineXMR has about 13,000 miners and charges a 1% pool fee. According to a screenshot from Archive.org last August, the pool only contributed to 34% of the hash rate of the XMR network. The rapid rise in the network’s hash rate has spooked some XMR enthusiasts, with Reddit user u/vscmm writing: “We need to talk with MineXMR to take some action right now! Please send an email for support@minexmr.com to MineXMR admins to take action; a 51% pool is not in the best interest of the community or the pool.” If a 51% attack were to occur, the bad actors involved could potentially overturn network transactions to double-sp...
- 1
- 2