Security
DeFi-ing exploits: New Chainalysis tool tracks stolen crypto across multiple chains
Blockchain analytics firm Chainalysis has released a new tool to track transactions across decentralized finance (DeFi) protocols and multiple blockchains. Chainalysis launched a beta version of its Storyline software on Wednesday. Touted as a “Web3-native blockchain analysis tool,” Storyline aims to track and visualize smart contract transactions with a focus on nonfungible tokens (NFTs) and DeFi platforms. This is in line with the growing popularity and prevalence of NFTs and DeFi in the cryptocurrency space over the past year. Chainalysis provides blockchain analysis and annual reports on cryptocurrency crime trends and other analytics. The ever-changing landscape has seen DeFi and NFTs become important cogs in the ecosystem, with Chainalysis estimating the two sectors account for more ...
What Happens When Cybercriminals Impersonate CEOs?
Image sourced from Feed Navigator. Traditional payment fraud has been rife for some time, where the cybercriminal impersonates the CEO, or other senior members of staff, to convince the finance department to make an urgent payment to either a new supplier or update their bank details. Now over the past month, there has been an increase in an evolved method of change of bank details or payment fraud cyber-attack. This new trend involves an internal change of bank details, mostly for the CEO. The change of bank details fraud uses fake banking confirmation letters and the trust of finance people to update an existing supplier’s details. The growing number of successful attacks have proven to be very costly to businesses of all sizes. Owing to this, many businesses have now implemented stronge...
DeFi attacks are on the rise — Will the industry be able to stem the tide?
The decentralized finance (DeFi) industry has lost over a billion dollars to hackers in the past couple of months, and the situation seems to be spiraling out of control. According to the latest statistics, approximately $1.6 billion in cryptocurrencies was stolen from DeFi platforms in the first quarter of 2022. Furthermore, over 90% of all pilfered crypto is from hacked DeFi protocols. These figures highlight a dire situation that is likely to persist over the long term if ignored. Why hackers prefer DeFi platforms In recent years, hackers have ramped up operations targeting DeFi systems. One primary reason as to why these groups are drawn to the sector is the sheer amount of funds that decentralized finance platforms hold. Top DeFi platforms process billions of dollars in transactions e...
How blockchain archives can change how we record history in wartime
Decentralized blockchain technology has been around for a relatively short period of time, in the grand scheme of things, but its decentralized nature has the power to keep data and information out of the hands of censors looking to create a “safe” and “faultless” version of history. Blockchain is permissionless and literally owned by no one. So, while we can’t save the Alexandria libraries of the past, we can make sure the future is well equipped with the tools necessary to preserve historical records. Here we’ll look at some of the ways nonfungible tokens (NFT) and blockchain technology have been used for keeping archives, the potential downfalls of such technology, and what the future holds for blockchain-based storage systems. NFTs and archives While many current use cases ...
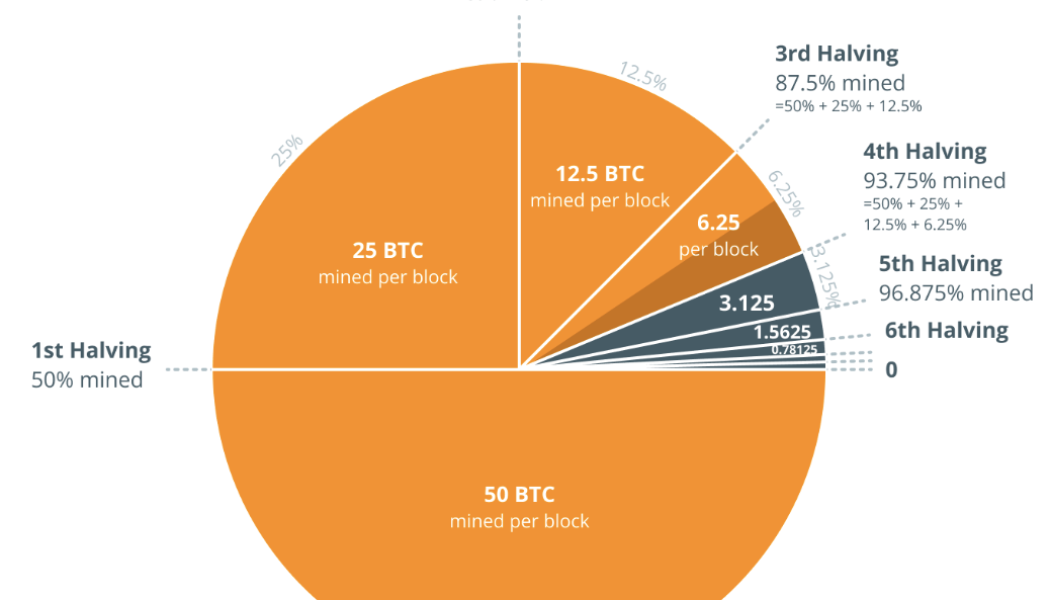
Bitcoin celebrates halfway to the halving with new hash rate record
Bitcoin (BTC) marks a milestone mining journey on Thursday, crossing the halfway point on the way to its next halving. In Block number 735,000, mined at approximately 10:29 UTC, Bitcoin crossed the halfway point to the next halving. The block was mined by Poolin, earning 0.16215354 BTC ($6,402.45) in fees. Halvings occur every 210,00 blocks, and May 5 marks the cross-over point into the second leg of 105,000 blocks. For some Bitcoiners, such as Samson Mow, the Bitcoiner pioneering Bitcoin nation-state adoption, the halving is a reminder to stack more SATs: WE ARE HALFWAY TO THE NEXT HALVING AND YOU HAVEN’T STACKED ENOUGH #BITCOIN YET. — Samson Mow (@Excellion) May 5, 2022 The halving cycle is a unique device that envelops the Bitcoin issuance rate. As the Cointelegraph Cry...
Polkadot launches cross-chain messaging system to solve blockchain’s bridge problem
Blockchain platform Polkadot has launched a new cross-chain communications protocol, saying it will do away with cumbersome bridging mechanisms that have cost the crypto industry billions in cyber attacks. The newly launched XCM messaging system is intended to promote Polkadot’s multichain ecosystem, which is being built on the premise of full interoperability. XCM channels are said to be secured at the same level as Polkadot’s central hub, dubbed Relay Chain, and are also available for use by parachains. In other words, XCM will enable communication between parachains themselves as well as smart contracts. Future iterations of XCM will allow messages to be sent between parachains without having to be stored on the Relay Chain, thereby improving scalability and eliminating governance...
Has New York State gone astray in its pursuit of crypto fraud?
The Empire State made two appearances on the regulatory stage last week, and neither was entirely reassuring. On April 25, bill S8839 was proposed in the New York State (NYS) Senate that would criminalize “rug pulls” and other crypto frauds, while two days later, the state’s Assembly passed a ban on non-green Bitcoin (BTC) mining. The first event was met with some ire from industry representatives, while the second drew negative reviews, too. However, this may have been more of a reflex response given that the “ban” was temporary and principally aimed at energy providers. The fraud bill, sponsored by State Senator Kevin Thomas, looked to steer a middle course between protecting the public from scam artists while encouraging continued innovation in the crypto and blockchain sector. It...
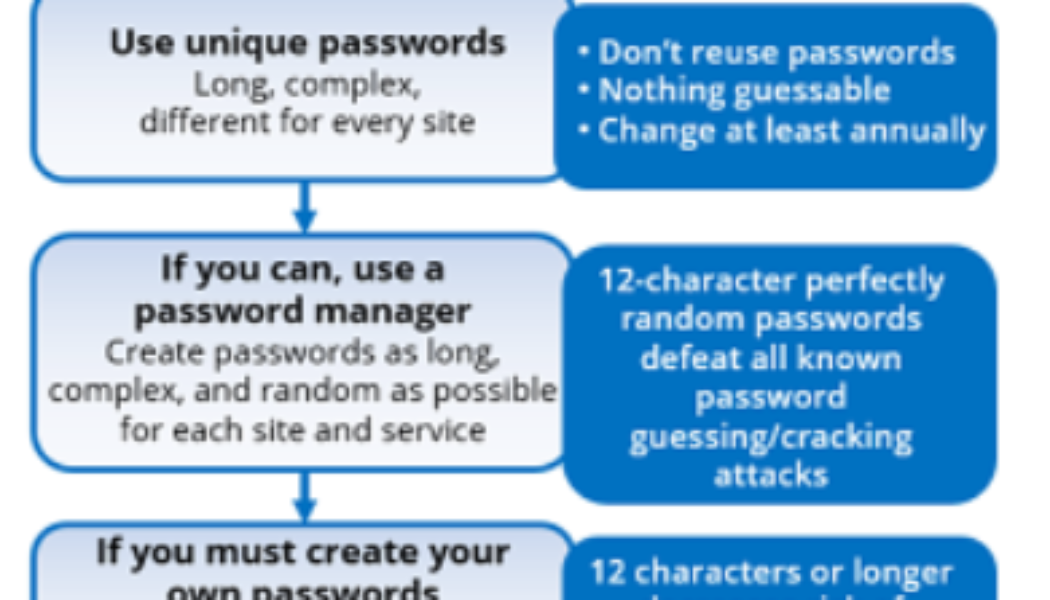
How Hackers Get Your Passwords & How to Defend Yourself
Sourced from Travellers Despite the world’s best efforts to get everyone off passwords and onto something else (e.g., MFA, passwordless authentication, biometrics, zero trust, etc.) for decades, passwords have pervasively persisted. Today, nearly everyone has multiple forms of MFA for different applications and websites AND many, many passwords. The average person has somewhere between three to seven unique passwords that they share among over 170 websites and services. And, unfortunately, those passwords often get stolen or guessed. This is why I recommend the following password policy guide: Most computer security experts agree with these policy recommendations, but more than a few readers might be shaking their heads, especially at the recommendations to use 20+ character passwords/pass...
Omnis Security from NETSCOUT: Protect Your Network from the Threats You Can’t See
On 09 December 2021, the world was alerted to the Log4j vulnerability [CVE-2021-44228 aka Log4Shell]. It is likely that threat actors already knew about the vulnerability before this date, says Tom Bienkowski, NETSCOUT Product Marketing Director, because it’s been reported that the vulnerability had been exposed much earlier in Minecraft chat forums. How does Log4j work – and what lessons does it bring? Log4j, which is open-source software provided by the Apache Software Foundation, records errors and routine system operations and sends diagnostic messages about them to system administrators and users. A common example of Log4j is when a user types in or clicks on a bad weblink and they receive a 404 error message. The web server running the domain of the attempted weblink sends a message ...