Top Stories
Demand for African Developers “At An All-Time High” Says Google
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
Vodacom is Tackling Food Insecurity in SA Through This New Initiative
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
7 Great Security Practices to Make Sure Your Social Media is Safe & Private
Social media provides a world of opportunities for an organization or individual to promote and expand a brand. A powerful form of communication that uses the internet, social media can provide any organization with a strong global presence. Most organizations believe they must have a social media presence because these platforms and apps have billions of users and an audience that could have millions of potential prospects, customers, partners, employees, and advocates. Social media platforms enable an organization’s representatives and its followers to have interactions that involve sharing information, exchanging feedback, and creating content. Balancing “Social” and Security Social media can increase brand awareness and engagement with the public. It allows for a generally less-expensi...
All the Details About Ericsson’s New Edge Exposure Server Offering
Ericsson, the Swedish multinational telecom, has announced the launch of its new Edge Exposure Server, which can be used to enable new enterprise and consumer services through simple and enriched APIs for edge applications. According to Ericsson, 5G and edge computing are opening a world of new revenue opportunities across manufacturing, transport, gaming and mission-critical services. Combined they enable new services requiring low latency, high bandwidth and capabilities such as device processing and data offload. Edge computing consists of five technology areas including edge infrastructure, -user plane, -routing, -orchestration and exposure. Exposure makes network capabilities, such as location and quality of service, and data easily available for the ecosystem to innovate on to improv...
What are the Benefits of Mixing & Matching Your COVID Booster Shot?
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
SA Startup Bringing “Tap to Pay” to Africa’s Informal Sector Raises Millions
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
vivo V23 5G Launches in Kenya
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
Nigeria’s Paga Announces New Payments Deal with this Social Media Powerhouse
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. By clicking “Accept All”, you consent to the use of ALL the cookies. However, you may visit “Cookie Settings” to provide a controlled consent.
The Changing Landscape of MDM in the World of BYOD
Modern-day Mobile Device Management (MDM) solutions offer much more than basic device management features. The Bring your own device (BYOD) trend gained instant momentum when it was introduced to the corporate world in the early 2000s. The business world, which until then relied on company-owned devices, was pleased to accept the BYOD work environment that presented boons for both the employers and the employees. After maintaining a stronghold on the corporate world for several years, businesses began re-evaluating the BYOD business model in terms of data security. The main concern was if the corporate data was ever completely safe on employees’ personal devices, especially outside office premises. Today, the most common question remains – “is BYOD now a thing of the past?” The...
Push-To-Talk: Why Practically Every Frontline Workforce Needs It
The Push to Talk (PTT) technology has helped frontline employees communicate on-site for the past few decades. A majority of global businesses, especially after the dawn of enterprise mobility depend on a field workforce to deliver the expected results. Several industries including logistics and transportation, construction, mining, warehousing, healthcare, retail, etc. have deskless workers that operate from remote on-field locations. Seamless corporate communication is imperative for high operational efficiency, which is why businesses have to ensure that the communication with their frontline employees is always streamlined. Mobile devices have been a part of the corporate world for decades, yet frontline employees face certain barriers to effective communication. Communication Barriers...
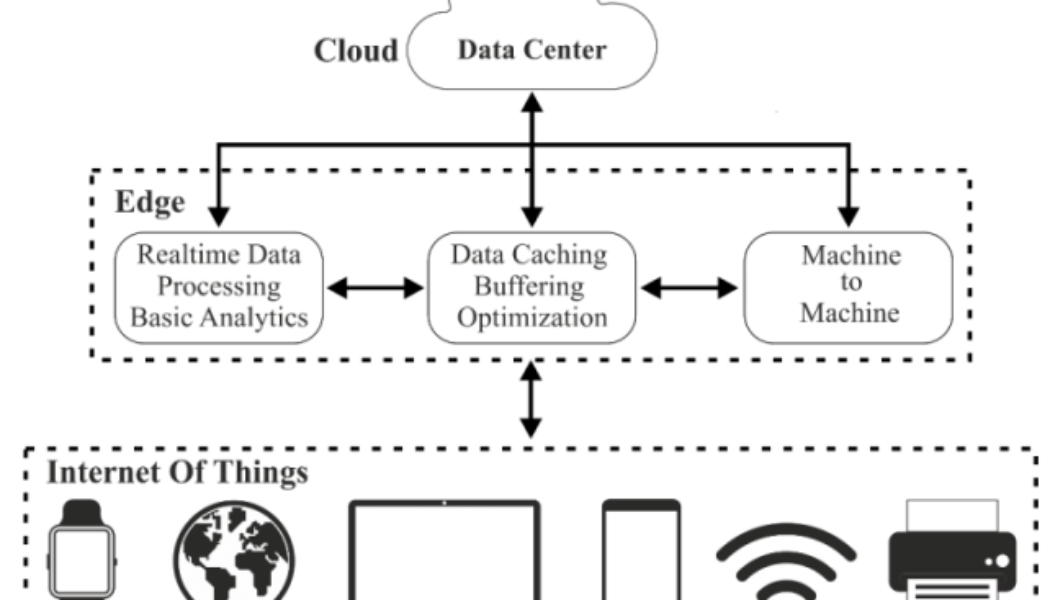
How Application Layer Attacks Impact Edge Architecture
As we approach the two-year mark since the start of the COVID-19 pandemic, IT and security teams continue to grapple with massive changes it has wrought on enterprise networks. One of the biggest changes has been the need to support remote work, which initially was believed to be a temporary strategy necessary to keep businesses operational during the pandemic. However, companies increasingly are realizing that remote work is here to stay. In fact, 87 percent of workers say they want to continue working remotely after the pandemic. And 42 percent of workers say they’ll look for jobs elsewhere if their current company doesn’t continue to offer long-term remote work options. The need to support remote work and deal with other pandemic-related stresses has led many companies to...
Hornetsecurity global ransomware survey reveals the ‘stinging truth’
Ruan du Preez, Vendor Alliance Director – SA and SADC from Networks Unlimited, an Exclusive Networks company Shows backup solutions are critical to fight malware A recent global survey by Hornetsecurity, a leading European email cloud security provider, has shown that a staggering one in five companies is likely to fall victim to a ransomware attack, in which malicious software (malware) is used with the threat to either publish data, or block access to data or a computer system until the victim pays a ransom fee to the attacker. “This is particularly pertinent in South Africa, which was named as being in the top three worst-affected countries in Africa – together with Egypt and Tunisia – as regards targeted ransomware attacks for the first quarter of 2021,” says Ruan du Preez, Vendo...