hackers
Multichain under fire from users as hacking losses grow to $3M
Hackers have continued to exploit a critical vulnerability in the cross-chain router protocol (CRP) Multichain that first appeared on Jan 17. Earlier this week, Multichain urged users to revoke approvals for six tokens to protect their assets from being exploited by malicious individuals. However Multichain’s announcement on Jan. 17 encouraged more hackers to try the exploit. One stole $1.43 million, another offered to return 80% while keeping the rest as a tip. According to Tal Be’ery, the co-founder of the ZenGo wallet, the stolen amount has now risen to $3 million. The @MultichainOrg hack is far from being over.Over the last hours more than additional $1M stolen, rising the total stolen amount to $3M.One victim lost $960K!https://t.co/fYhYxUojB8 pic.twitter.com/Gvh5hB6t6s — Tal Be...
LCX loses $6.8M in a hot wallet compromise over Ethereum blockchain
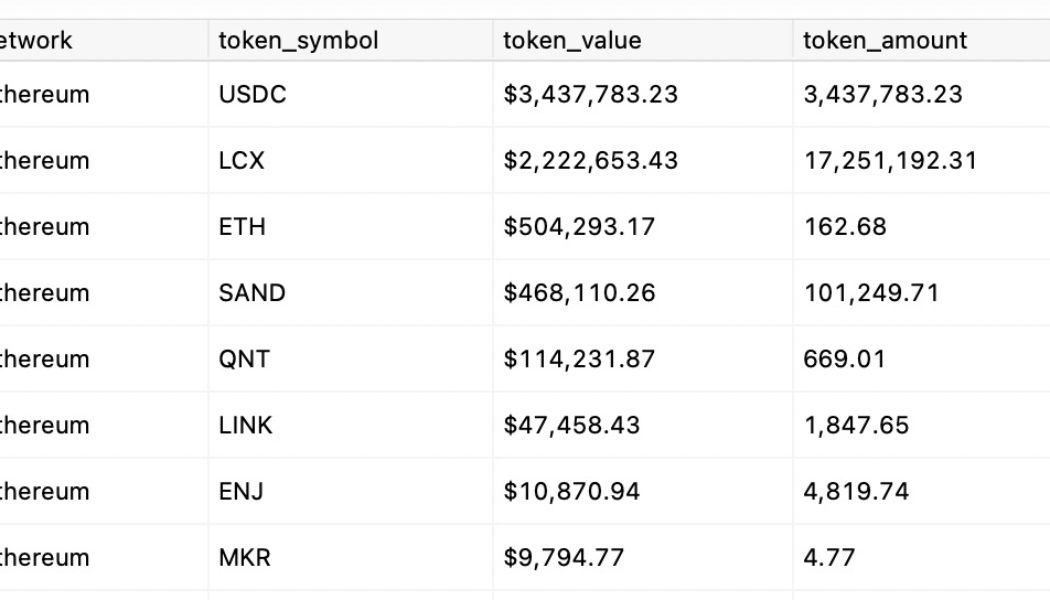
Liechtenstein-based crypto exchange LCX has confirmed the compromise of one of its hot wallets after temporarily suspending all deposits and withdrawals on the platform. The hack was first identified by PeckShield, a blockchain security company, based on the suspicious transfer of ERC-20 tokens from LXC to an unknown Ethereum wallet. hot wallet compromised? @lcx https://t.co/uL5a7oCFfM — PeckShield Inc. (@peckshield) January 9, 2022 The probable hot wallet compromise was soon confirmed by the exchange as it announced the loss of numerous tokens including Ether (ETH), USD Coin (USDC) and other tokens including its in-house LCX token. Ethereum blockchain based assets such as ETH, USDC, EURe, LCX and other assets have been moved to the Hacker ETH Wallet: 0x165402279F2C081C54B00f0E08812F...
Beware of sophisticated scams and rug pulls, as thugs target crypto users
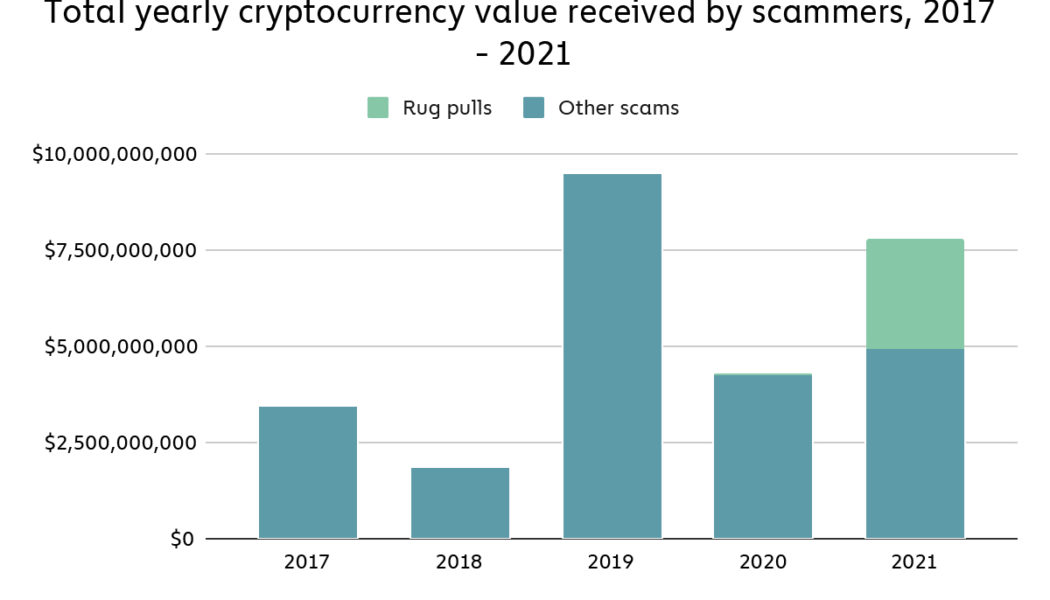
This year has been monumental for the cryptocurrency sector in terms of mainstream adoption. A recent report published by Grayscale Investments found that more than one-quarter of United States investors (26%) surveyed own Bitcoin (BTC), up from 23% in 2020. With the holidays around the corner, financial services provider MagnifyMoney also found that nearly two-thirds of surveyed Americans hope to receive cryptocurrency as a gift this year. While crypto’s growth is notable, there has also been an increase in the number of scams associated with digital assets. A Chainalysis blog post highlighting the company’s “2022 Crypto Crime Report” revealed that scams were the dominant form of cryptocurrency-based crimes by transaction volume this year. The post notes that over $7.7 billion ...
DeFi protocol Grim Finance lost $30M in 5x reentrancy hack
The decentralized finance (DeFi) protocol Grim Finance reported $30 million in losses due to a reentrancy exploit of the platform’s deposits. Grim Finance officially announced on Dec. 18 that an “external attacker” had exploited the DeFi platform, stealing “over $30 million” worth of cryptocurrencies. According to Grim Finance, the hack was an “advanced attack,” with the attacker exploiting the protocol’s vault contract through five reentrancy loops, which allowed them to fake five additional deposits into a vault while the platform is processing the first deposit. Grim paused all vaults after the attack to minimize the risk for future funds: “We have paused all of the vaults to prevent any future funds from being placed at risk, please withdraw all of your funds immediately.” Grim no...
Indian prime minister Modi’s hacked Twitter account attempts BTC scam
The official Twitter account of Indian Prime Minister Narendra Modi got compromised earlier today, which was then used to share misleading information about the mainstream adoption of Bitcoin (BTC) and redistribution of 500 BTC among the Indian citizens. On Dec. 10, Modi said in a virtual event virtual summit hosted by US President Joe Biden that technologies such as cryptocurrencies should be used to empower democracy and not undermine it: “By working together, democracies can meet the aspirations of our citizens and celebrate the democratic spirit of humanity.” While the long-awaited Lok Sabha Winter Session, a parliamentary meetup intended to discuss the legality of cryptocurrencies in the region, did not conclude the government’s stance on crypto, hackers from unknown origins man...
AscendEX loses $80M following ERC-20, BSC, Polygon hot wallet compromise
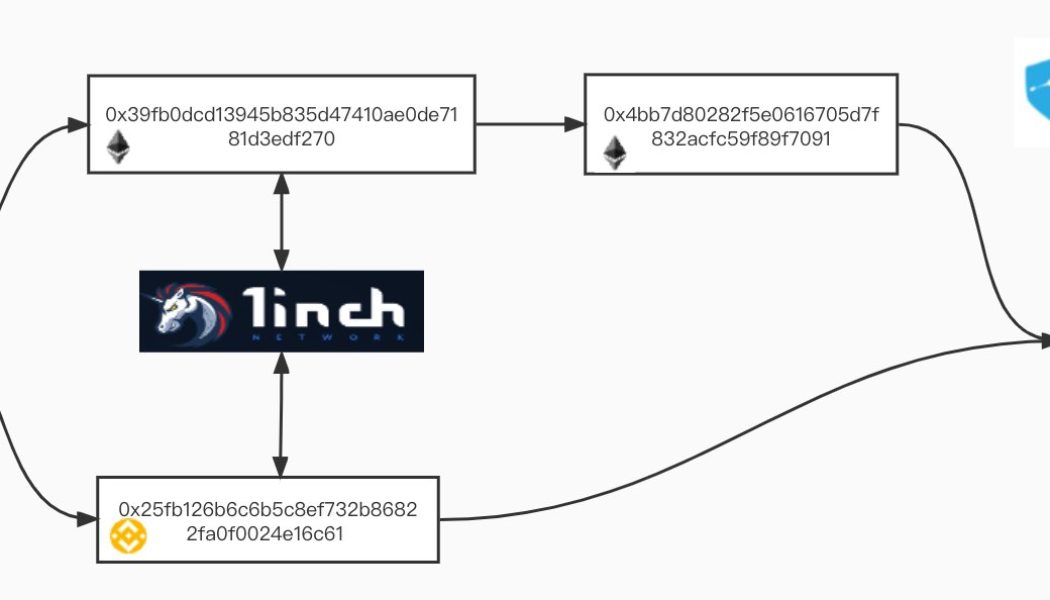
Crypto trading platform AscendEX suffered a loss of $77.7 million in a hot wallet compromise that allowed hackers to access and transfer tokens hosted over the Ethereum (ETH), Binance Smart Chain (BSC) and Polygon (POLY) blockchains. Soon after realization, AscendEX proactively warned its users about the stolen funds, confirming that the hackers were not able to access the company’s cold wallet reserves. 22:00 UTC 12/11, We have detected a number of ERC-20, BSC, and Polygon tokens transferred from our hot wallet. Cold Wallet is NOT affected. Investigation underway. If any user’s funds are affected by the incident, they will be covered completely by AscendEX. — AscendEX (@AscendEX_Global) December 12, 2021 According to PeckShield, a blockchain security and data analytics company, around $60...
The Most Vulnerable IoT Devices: Think Before You Buy This Black Friday
With the shopping season approaching, it’s likely that internet-connected gadgets and toys will be a popular item on many users’ wish lists, as more than 88% of people use IoT (Internet of Things) devices in their households. However, cybersecurity experts warn: Internet of Things devices can quickly go from fun to creepy, depending on how hackable they are. “Enormous Black Friday discounts can rush customers into buying some very questionable gadgets. However, Internet of Things devices is widely known among experts for low-security measures they usually have installed. There is a joke going around: ‘The S in IoT stands for security’. So, it’s best to think before bringing any new IoT device to your household, as it can easily compromise the whole network,” says digital security expert at...
How to Prevent Further CyberAttacks on Businesses & Government Departments
Image sourced from Finance Times. The recent ransomware attacks on the Department of Justice and Constitutional Development (DoJ) and the South African National Space Agency (Sansa) is a testament to the sophistication and aggressiveness of cybercrime in South Africa. In response to these attacks, organisations need to devise a preventative plan of action. “With South Africa having the third-highest number of cybercrime victims worldwide, and the biggest threat being ransomware, businesses are prone to being victims of ransomware traps unknowingly. In such cases, cyber-criminals pose as credible agencies with the intent of luring organisations to their demise,” says Maeson Maherry, CEO and co-founder of LAWtrust. What are Ransomware Attacks? Ransomware attacks are cyberattacks where a cybe...
IoT is One of Medicine’s Biggest Tools – Also Its Weakest Security Link
Image sourced from HP Consultant. /* custom css */ .tdi_4_0e2.td-a-rec-img{ text-align: left; }.tdi_4_0e2.td-a-rec-img img{ margin: 0 auto 0 0; } Healthcare has always been on the cutting edge, with hospitals and healthcare providers typically quick to embrace any innovation that will translate into better, more efficient, more affordable care. From microscopic pill cameras and implantable devices to laser surgery and advanced monitoring techniques, medical technology is all about creating the best possible patient outcome. But when it comes to the latest wave of innovative products, powered by always-on, always-connected internet of things (IoT) technology, there are growing concerns that security issues may eventually harm medical institutions or the patients themselves. /* custom css */...
Minister urges media to create fact-checking desks against fake news
Minister of Information and Culture, Alhaji Lai Mohammed, has advised media organisations to set up special desks for fact-checking in order to guard against being misled by fake news and misinformation. He gave the advice in Abuja yesterday when he hosted the editorial board of the Guardian Newspaper on a courtesy visit. The minister urged media organisations in Nigeria to take his suggestion seriously, noting that establishment of a special desk for fact-checking will curb the problem of fake news and enable the citizens to separate fact from fiction. He said in the era of fake news and misinformation, the media has a duty to get its facts right and ensure that charlatans and hackers do not dominate the media space, as it is increasingly becoming the case in the country. Mohammed said: “...
How Hackers are Taking Advantage of the COVID-19 Vaccine Rollout
Image sourced from TimesLIVE Cybercriminals are well known for taking advantage of any opportunity. The largest vaccine rollout in history is no exception, with hackers now finding ways to target the supply chain. Understanding why the COVID-19 vaccine supply chain being targeted and how to protect against such attacks is vital for IT leaders who understand that healthcare and cybersecurity must now go hand in hand. Understanding the impact of the COVID-19 vaccine supply chain on healthcare cybersecurity The healthcare sector underwent several significant shifts during the pandemic. These shifts included a move toward offering telehealth services on a large scale, setting up remote, temporary COVID-19 testing and vaccination sites, and large-scale development, manufacturing, and distr...