NETSCOUT Cybersecurity
Omnis Security from NETSCOUT: Protect Your Network from the Threats You Can’t See
On 09 December 2021, the world was alerted to the Log4j vulnerability [CVE-2021-44228 aka Log4Shell]. It is likely that threat actors already knew about the vulnerability before this date, says Tom Bienkowski, NETSCOUT Product Marketing Director, because it’s been reported that the vulnerability had been exposed much earlier in Minecraft chat forums. How does Log4j work – and what lessons does it bring? Log4j, which is open-source software provided by the Apache Software Foundation, records errors and routine system operations and sends diagnostic messages about them to system administrators and users. A common example of Log4j is when a user types in or clicks on a bad weblink and they receive a 404 error message. The web server running the domain of the attempted weblink sends a message ...
NETSCOUT: The Long Tail of Adversary Innovation
Image sourced from Shutterstock. NETSCOUT’s ATLAS Security Engineering and Response Team (ASERT) observed a record-setting 5.4 million attacks in the first half of 2021, further confirmation that their “up and to the right” mantra would continue to hold true. As the findings from the 1H 2021 NETSCOUT Threat Intelligence Report show, the ongoing surge in DDoS activity is just one aspect of the dramatic global impact cyberattacks continue to have on private and public entities. “Cybercriminals are making front-page news launching an unprecedented number of DDoS attacks to take advantage of the pandemic’s remote work shift by undermining vital components of the connectivity supply chain,” stated Richard Hummel, threat intelligence lead, NETSCOUT. “Ransomware gangs added triple-extortion ...
Today’s New Business Normal Creates Threat Opportunities
Image sourced from Feed Navigator. The COVID-19 pandemic forced businesses of all shapes and sizes to make rapid changes in how they operated, with employees predominantly working remotely and sensitive data and systems being accessed from outside the office. For many, this triggered an increased reliance on remote-access infrastructure and cloud-delivered services. IT departments rushed to install, expand, or upgrade remote desktop access (RDA) servers, virtual private network (VPN) concentrators, and remote access routers to meet surging workforce demand for remote access to data centres. Moreover, widespread reliance on video conferencing apps forced many businesses to upgrade enterprise wide-area network and local-area network capacity, as well as to re-evaluate routing and DNS re...
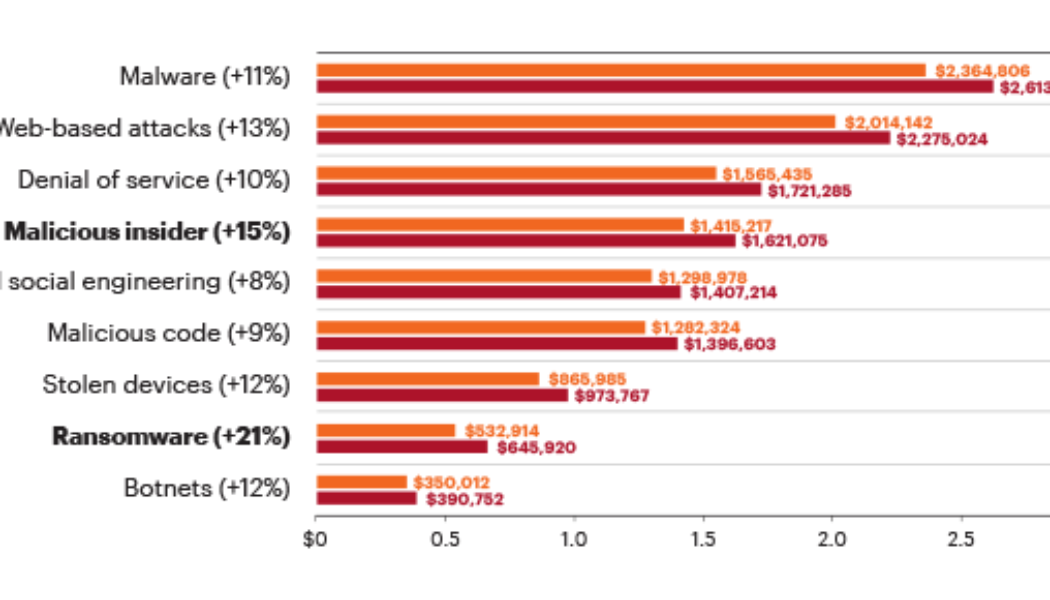
The High Cost of Cybercrime is Getting Higher
Image sourced from Finance Times. If cybercrime organizations could be publicly traded, we’d have an instant new multibillion-dollar industry sector. Indeed, cyber threats have become so pervasive that U.S. President Joe Biden recently signed an executive order aimed at improving federal cybersecurity in the wake of multiple significant cyberattacks, including the ransomware attack that shut down the Colonial Pipeline. Meanwhile, a broad coalition of experts in the industry, government, law enforcement, civil society, and international organizations have joined together in the Ransomware Task Force to build a framework for combatting ransomware. Ransomware attacks are only one method, however. Threat actors also use distributed denial-of-service (DDoS) attacks to ratchet up the p...
Surging DDoS Attacks Drive Growing Demand for Third Party Protection Services
Image sourced from Shutterstock. As the global workforce largely shifted to work-from-home in response to the COVID-19 pandemic, reliance on online services soared. Many businesses were able to successfully pivot to this new normal as remote connectivity allowed access to vital systems and data. But as is often the case, no good deed goes unpunished. As the latest NETSCOUT Threat Intelligence Report shows, cybercriminals have exploited new vulnerabilities created by remote work across a wide variety of vertical industries. Making matters worse, perpetrators no longer have to be particularly technology-savvy in order to pull off attacks. Today, it is easy and relatively inexpensive to access sophisticated attack tools via for-hire services: A cottage industry has sprung ...